Provide Secure, Convenient Access for Your Growing Enterprise Workforce
WSO2 IAM simplifies secure workforce access to business resources, empowering employees and contractors while safeguarding against threats.
Unlock Secure Workforce Productivity
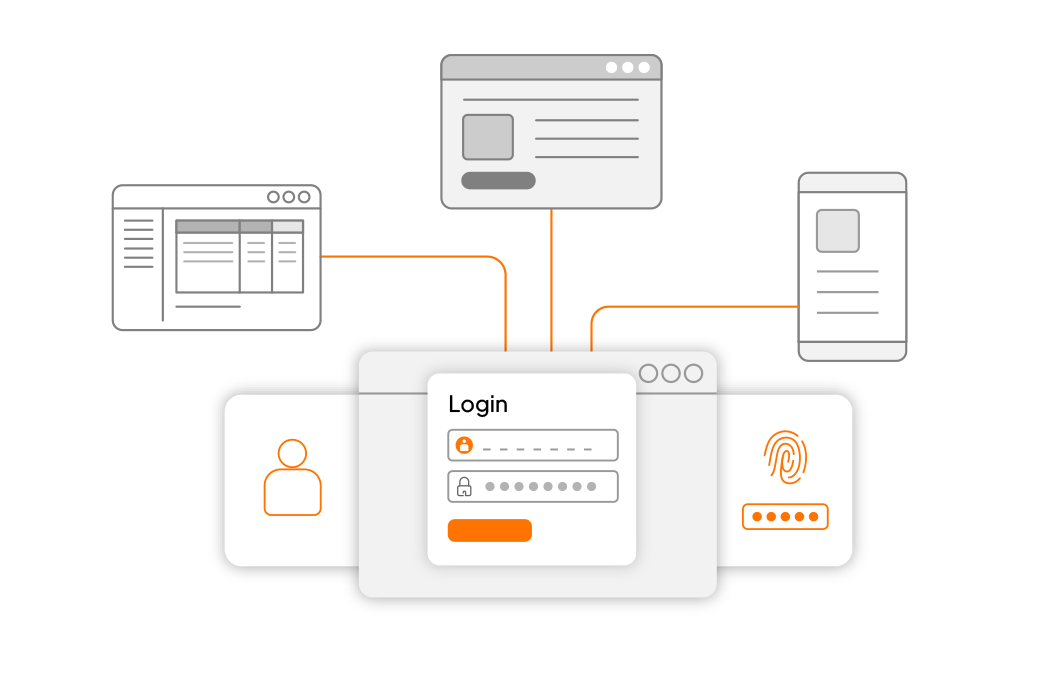
Access Apps Effortlessly and Securely
- Enable your workforce with Single Sign-On (SSO) for the low-friction, streamlined access they need while maintaining robust security
- Integrate access to business applications in minutes using popular standards such as OpenID Connect and SAML

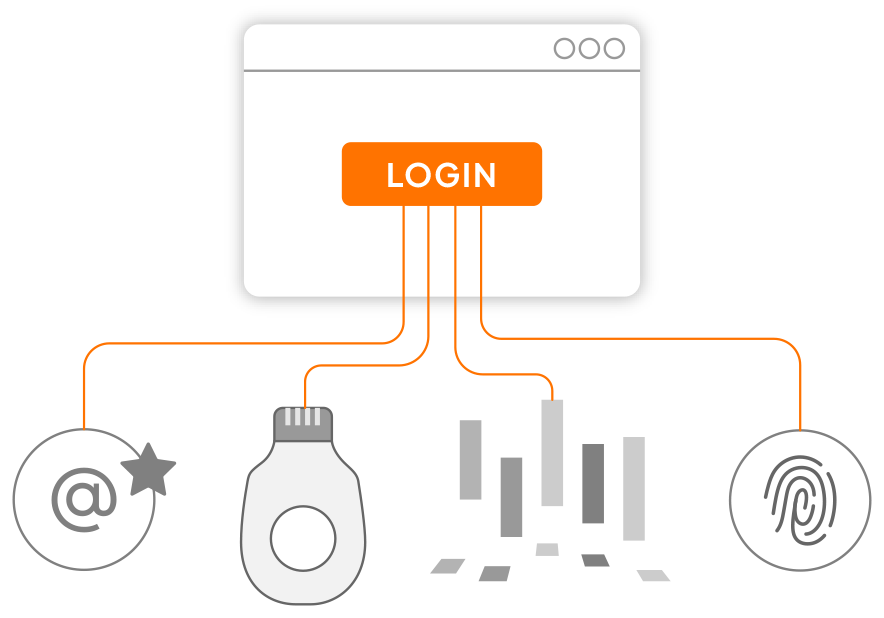
Eliminate Passwords
- Give your users the option to log in with innovative and secure passwordless authentication
- Leverage email magic links, FIDO2 compliant passkeys or security keys such as Yubico or Google Titan, or even biometric solutions such as TypingDNA
- Choose the best passwordless methods for your use cases

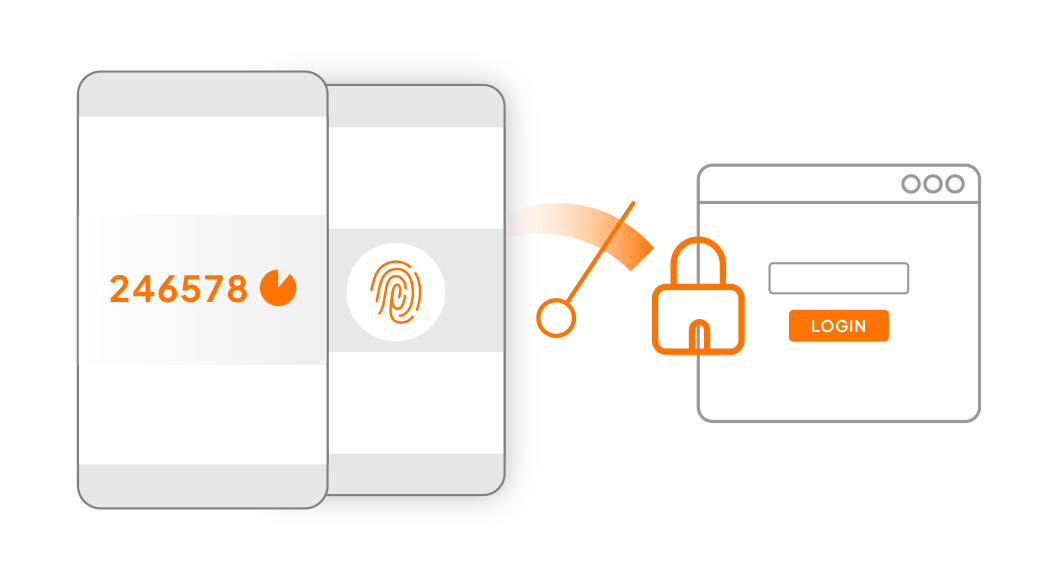
Apply Right Amount of Security
- Trust your security policy to adapt as needed with automatic assessment of risk conditions.
- Authentication processes dynamically adapt with stronger security measures, such as multi-factor authentication using authenticator apps or one-time passwords, when configurable security thresholds are exceeded.

Onboard Users and Integrate Apps Seamlessly

Automate User Management
- Use our integrated cloud directory to easily manage your users, or integrate your own user repository
- Easily allow users to manage their profile, reset their passwords, and more with an out-of-the-box user portal
Provision Access for the Right Apps to the Right People
- Set up federated access to your apps quickly, leveraging our built-in standards-based identity provider, or use your own
- Streamline access control for employees or contractors based on role, department, location, or other attributes
Operate in the Cloud, On-premises or in Hybrid Environments

IDaaS Deployment for Speed and Simplicity
- Get up and running instantly with our multi-tenant SaaS solution. Add your critical cloud-based business applications in minutes.

Run it yourself or use our private cloud deployment
- Use self-hosted software or let us host it for you. Address requirements such as integrating with Windows desktop authentication or legacy solutions.
Secure access Priced Affordably for your Growing Business

Licensing that works with you
- From a compelling pricing model, to flexible pay-as-you-go licensing options, our solution gives your organization the technology you need with a financial model that’s equally appealing.

One Solution for Your Internal Workforce and Your External Consumers
- Organizations that cater to external users benefit from built-in consumer IAM capabilities that can quickly add powerful user management and authentication features to your consumer-facing applications.