How To Optimize Your GDPR Strategy: Some Best Practices

- Sagara Gunathunga
- Director - WSO2
As we get closer to the General Data Protection Regulation (GDPR) compliance deadline of May 25, 2018, organizations are eager - more than ever before - to explore possible optimization strategies. This article gives an overview of optimization strategies and the topmost best practices that organizations can adopt, with an in-depth explanation of technology related optimization strategies in particular.
To begin with, we need to have a clear understanding about what we are hoping to optimize i.e. factors to be optimized and how we can optimize each factor. In the context of GDPR, we can identify a number of factors to be optimized but there are three vital factors we must be taken into consideration.
- Time: optimization process should minimize the time taken for GDPR compliance.
- Cost: optimization process should minimize the cost associated with GDPR compliance.
- Complexity: optimization process should aim to reduce the complexity of the solution, additionally a less-complex system means lower maintenance costs and flexibility for future changes.
Considering the fact that GDPR is a very broad regulation, it’s quite difficult to discuss how an organization can optimize time and cost in terms of the overall GDPR compliance strategy. Hence, I discuss each key aspect and their respective optimization factors separately. A high level breakdown of these aspects consists of people, process, and technology.
- People: GDPR compliance involves a set of mandates that needs to be exercised on the people associated with a particular organization. This includes staff, contractors, various service providers, etc. For example, the organization must ensure that there is no unauthorized access to personal data. Any staff member/ individual who manages personal data must have a thorough understanding about the privacy of users and whether or not legitimate grounds for storing this data exists.
- Process: GDPR mandates a thorough review of an organization’s personal data protection process and organizations are expected to make the necessary adjustments if needed, so as to honor the privacy and rights of individuals associated with the organization.
- Technology: review of existing tools and systems for data protection and privacy standards is mandatory. In addition, an organization may need to use new technologies to ensure the protection of personal data and enable facilities granted by GDPR for individuals.
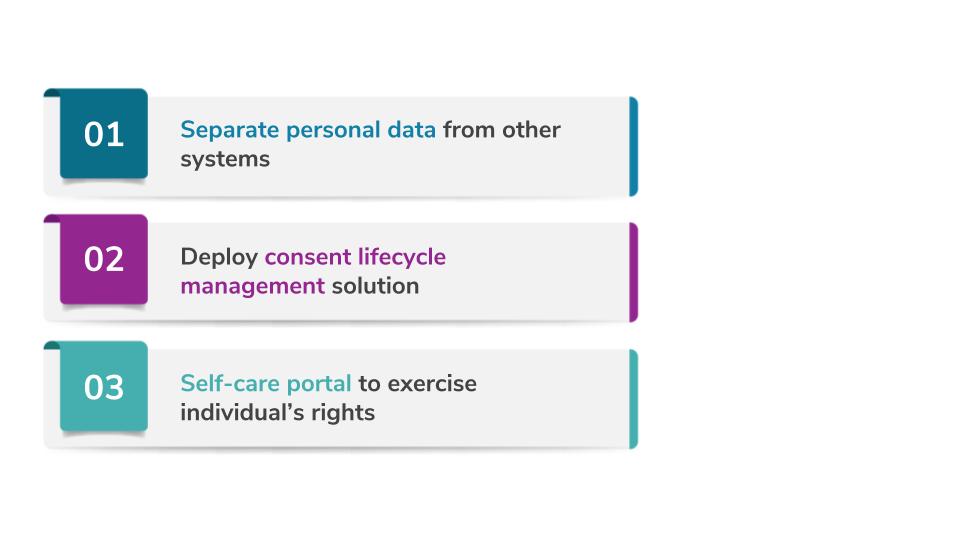
As mentioned in the introduction, this article explores three topmost best practices, among many, and how technology can be used to optimize time, cost, and complexity of an organization’s GDPR strategy. These best practices include:
Best Practice 1 - Separate Personal Data from Other Systems
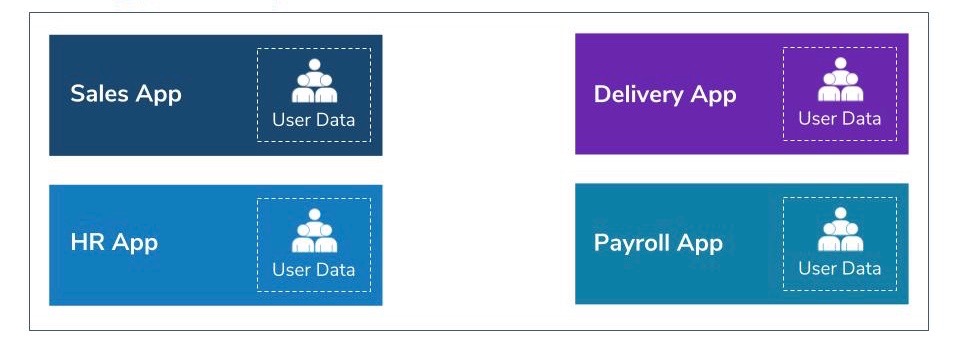
The following diagram is a simplified version of enterprise systems with four components. As an example, let’s imagine this is a system related to an online shipping company, which enables people to order goods online and have them delivered to a location of their choice.
The components of this system include:
- Sales App: facilitates the placing of online orders, storage and processing of information related to each transaction such as details of the items ordered, details of the individual who made the order, and payment details.
- Delivery App: coordinates delivery activities of items ordered with various delivery channels and enables individuals to check the status of items ordered.
- HR App: handles all people related aspects of the organization’s employees.
- Payroll App: used for employee payroll management.
Although each of above systems are meant to handle different operations of the organization, all of them consist of user management capabilities because that is a mandatory requirements. For example, the Sales App cannot operate without tracking individuals who place orders and similarly the Delivery App cannot operate without contact and delivery address details. However, these processes could result in duplicating personal data in several places, which in-turn leads to several issues under GDPR:
- Several systems storing personal information means the organization has to invest in protecting each and every system with maximum security to ensure personal data protection.
- The existence of numerous personal information points means increased maintenance and modification costs because the organization has to modify several points to support privacy and security standards.
- Extra effort is needed to synchronize changes of personal data which is a clear overhead and increases the overall cost.
- Multiple personal information points also increases the probability of data breaches, since an attack on any system can cause a significant data breach.
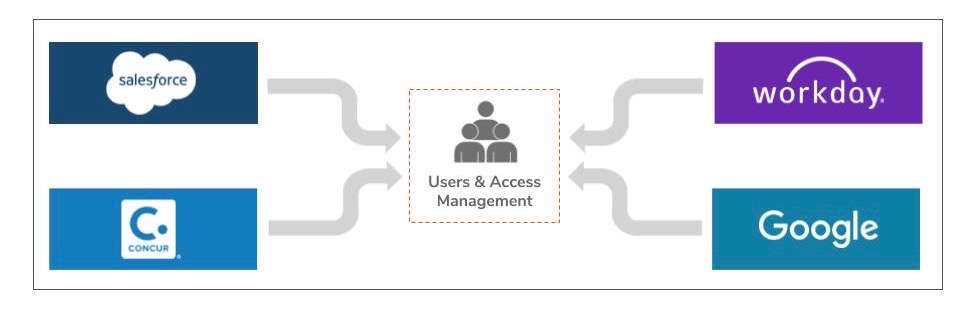
The solution to all these issues is to isolate personal information in a separate system. These systems are generally referred to as “Identity and Access Management” solutions and primarily handle users, their permission, and capabilities. After introducing an Identity (user) and Access Management system (IAM), the system architecture will appear as follows:
You may be wondering how the Sales App or Delivery App can perform their intended tasks without user information? The answer is that instead of locally storing a copy of personal data, each system requests for personal data from a centralized Identity (user) and Access Management (IAM) system in an on-demand manner. The Identity (user) and Access Management system are responsible for providing each system with the minimum required personal data as a temporary secure token. Generally these secure tokens are meant to be deleted after consumption. There are several industry-proven secure protocols and secure tokens formats that are able to perform the above mentioned tasks.
There’s another angle to this problem. Currently all organizations are moving to cloud services due to the many benefits but this also causes organizations to duplicate their personal information on the cloud service. GDPR terminology defines this practice as data sharing among two organizations and correspondingly, the required data protection measures greatly increase. Is our solution still applicable in such a situation?
Fortunately the answer is ‘yes’ and this is not new, over the years cloud vendors have facilitated organizations to plug-in their corporate IAM systems into the cloud service as ‘trusted identity providers’. This eliminates the necessity of moving personal data into the cloud service and instead, the cloud service can operate based on secure tokens issued by the IAM system of an organization. Today, most cloud vendors support this pattern based on industry standards such as SAML and OpenID Connect protocols.
Best Practice 2 - Deploy Consent Lifecycle Management Solution
Consent is one of the lawful processing means under GDPR, and it is a common and widely applicable lawful processing means for commercial organizations. The following section provides a brief summary on how consent is used in the context of GDPR:
- The purposes for collection and processing of each data item have to be stated prior to data collection. This process requires clear and affirmative consent from the individual in question.
- It is mandatory to ensure that active consent for data processing is available before this process begins.
- Individuals have the right to review previously given consent and revoke it if required.
- Personal data sharing outside the organization must be based on consent.
- Data processing organizations must be able to demonstrate that they have active consent from an individual with the required metadata such as consent method, time, username, etc.
If organizations are to fulfill the above mentioned requirements, they must have the following capabilities in-place:
- Ability to prompt purposes and record consent from individuals.
- Ability to store consent securely and retrieve consent for demonstration.
- Ability to review and revoke previously given consent by an individual.
- An API that enables other data processing systems to check the availability of consent remotely.
- Portability of consent from one system to another.
- Visual aspects of consent according to GDPR guidelines.
These capabilities are known as “Consent Lifecycle Management”. As defined by GDPR compliance, an organization needs the complete set of consent lifecycle management features. Organizations can either deploy ready-made consent management modules that are generally available with the above discussed IAM solutions or build in-house consent lifecycle management features.
Best Practice 3 - Self Care Portal to Exercise Individual’s Rights
GDPR mandates that data processing organizations enable individuals to exercise a number of rights over personal data collected and stored by the organization. The following diagram demonstrates these individual rights with short descriptions:
One of best and simplest approaches that organizations can use to facilitate individual rights is to provide their users with a self-care portal, so that individuals themselves can login to this portal and exercise their rights. A self-care portal normally consists of the following features:
- Ability for individuals to login securely.
- Ability to review personal information stored in the system.
- Ability to modify and remove information stored in the system.
- Ability to review data processing activities carried out on their data.
- Ability to make processing restrictions and send messages to the organization.
- Ability to review previously given consent and revoke consent if required.
- Ability to download a copy of their personal data stored by the organization in a standard format.
Pros and Cons
When executing these best practices, organizations can choose from two options:
- Develop homegrown systems for each aspect, or
- Deploy an identity and access management (IAM) solution.
However, each option is not without its set of pros and cons, and I list them out below.
Developing homegrown systems for each aspect
Pros
- Fits an organization's needs better.
- Easy to customize and evolve.
Cons
- Requires considerable time and cost.
- Needs specialized technical skills.
- Lower support for industry standards.
- Maintenance overhead when keeping up-to-date with security vulnerabilities.
Deploying an identity and access management (IAM) solution
Pros
- Better cost and time optimization.
- Specialized skills not required.
- Out-of-the-box support for industry standards.
- Vendor/community provides security updates.
- Evolves with security and privacy standards.
Cons
- Requires some customizations or extensions to support an organization’s requirements.
- Can cause vendor-lock-in.
Given the many benefits, it is the second option of deploying an IAM solution which could provide better support to accelerate an organization’s GDPR compliance journey.
Summary
We began this article by dividing the GDPR compliance strategy into three distinct aspects: people, process and technology. After which we discussed three top best practices which can be adopted by organizations to optimize the time, cost, and the complexity of their GDPR strategy. We also looked at how an organizations can either build a home grown application for each of their systems or deploy a generally available IAM solution as possible execution approaches. Considering the pros and cons of each option, deploying a generally available IAM solution grants many benefits and provides pattern optimization for an organization’s GDPR compliance strategy.