Enable user attributes for OpenID Connect apps
# Enable user attributes for OpenID Connect apps
Asgardeo can share user attributes with applications. This guide explains how you share user attributes with OpenID Connect applications.
# Configure user attributes to share
Follow the steps given below to configure the user attributes from the Asgardeo Console and to share them with the application.
# Select user attributes
You need to first specify the user attributes required for an application. This ensures that when a user logs in, the application can only get access to the user information exposed through these attributes.
The user attributes are grouped by their specific scopes to ease the user attribute configuration process. You can add user attributes individually or all the attributes in the scope at once.
To add user attributes to the app:
On the Asgardeo Console (opens new window), go to Applications.
Select your application and go to its User Attributes tab. Here the user attributes are listed under their relevant scopes.
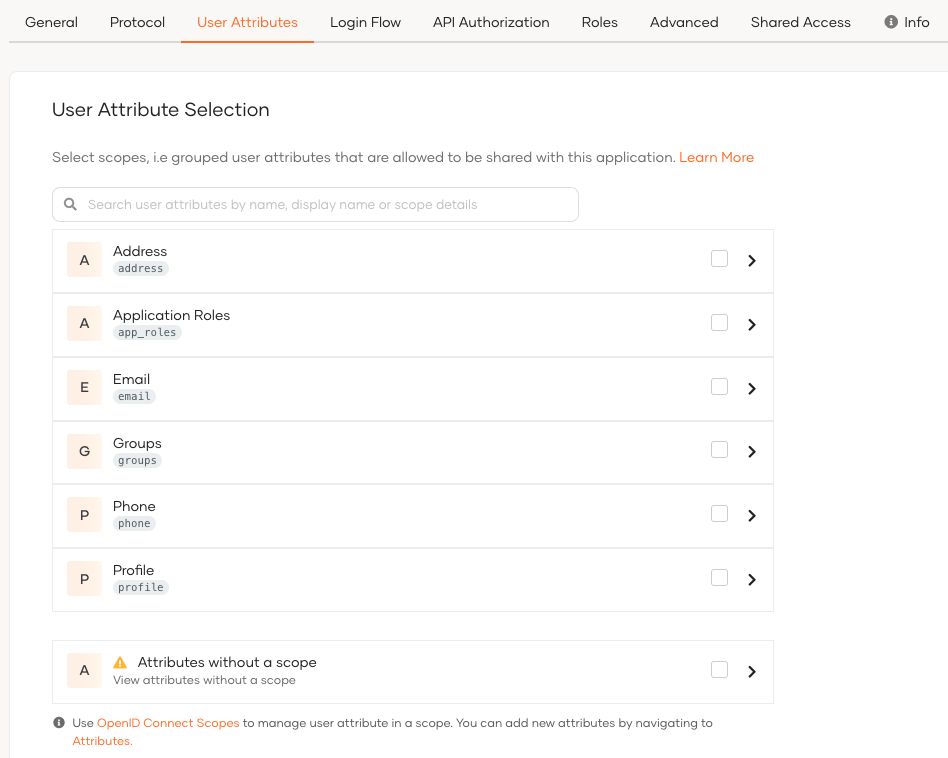
You can add user attributes using the following methods:
Add a group of user attributes by selecting the checkbox in front of the required scope. This will add all the user attributes grouped under the selected scope.
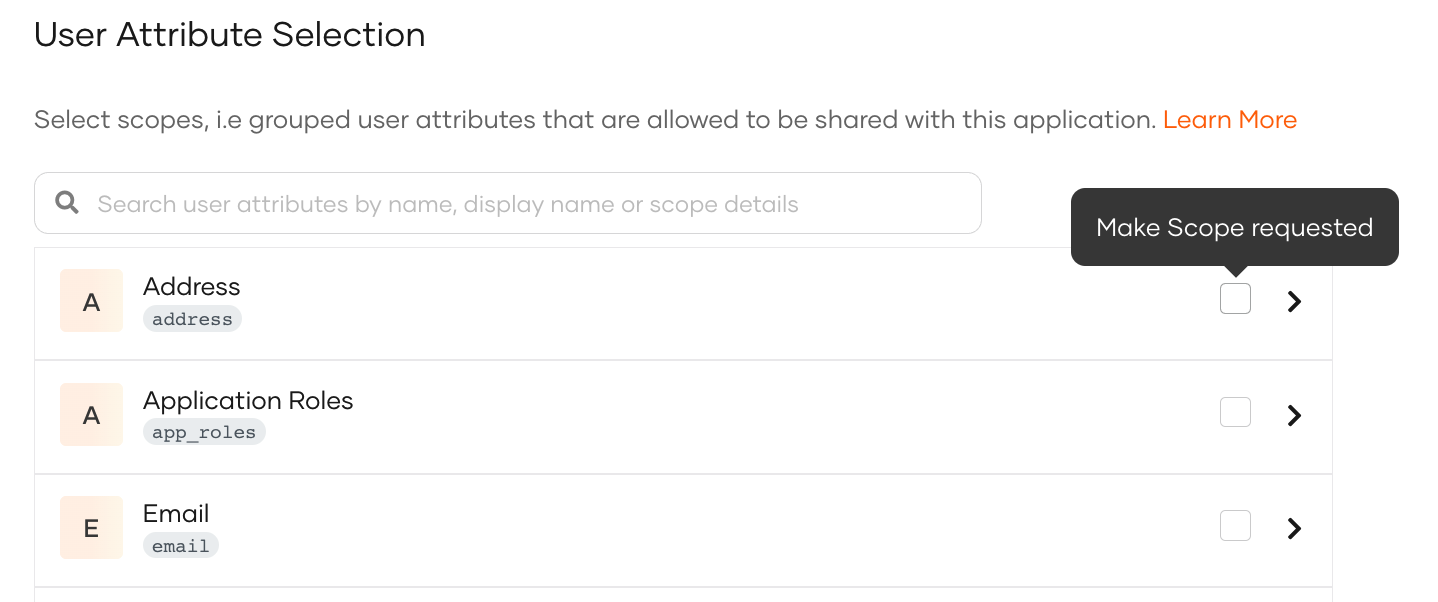
Add a single user attribute by expanding the required scope and selecting the user attribute you need from the expanded list.
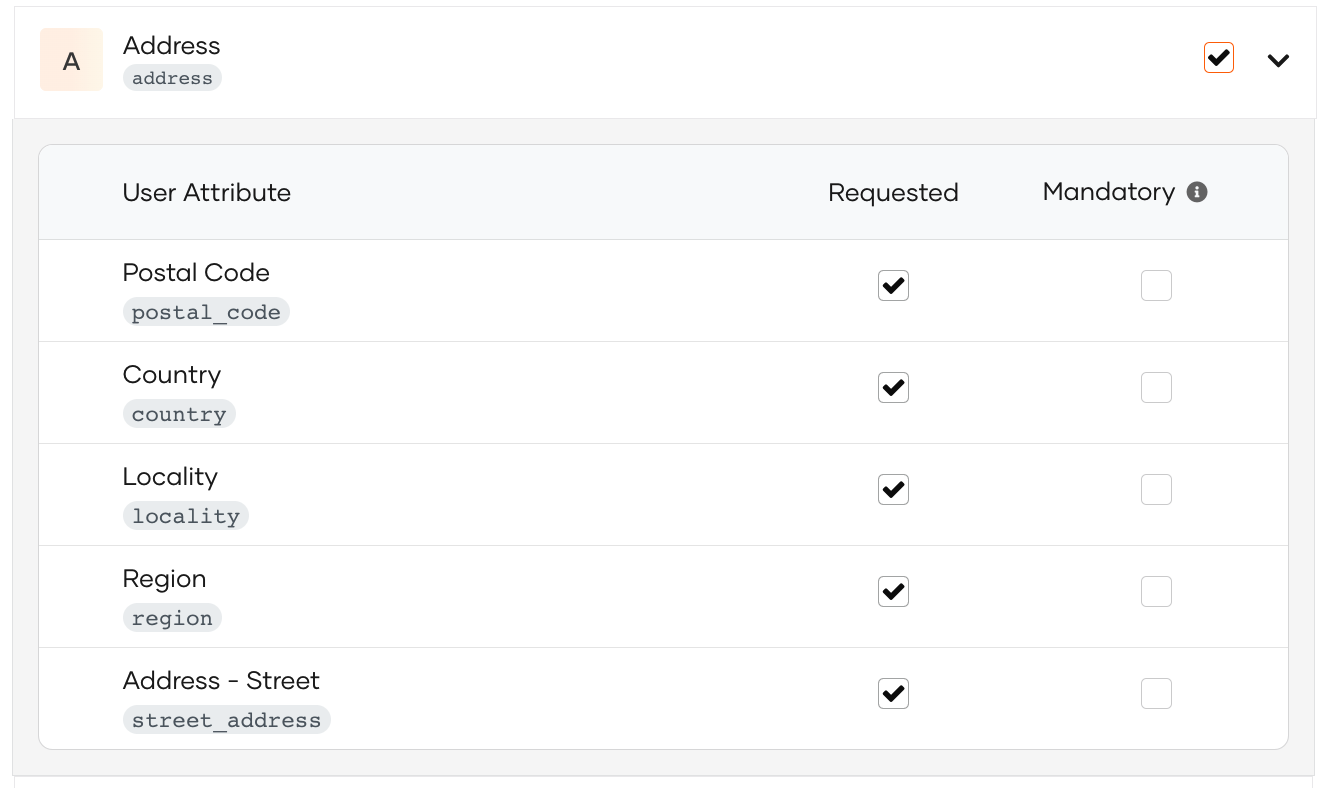
Click Update once you are done.
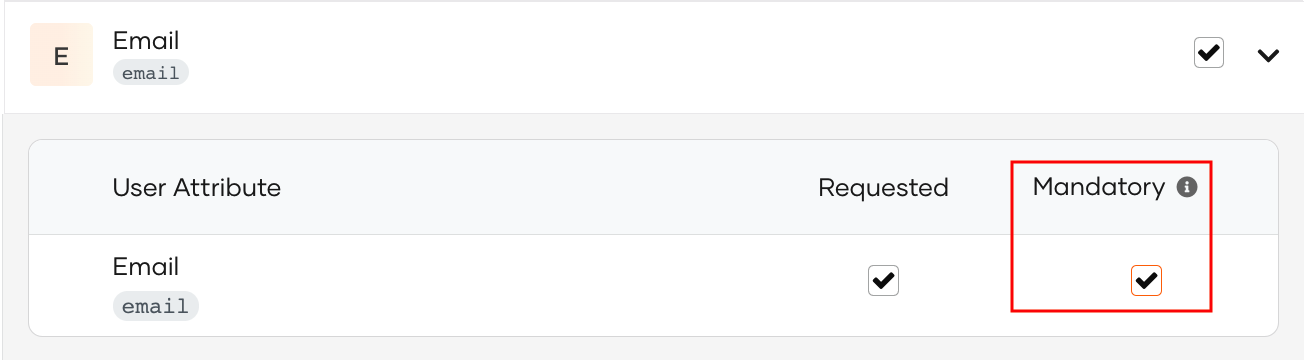
# Define mandatory user attributes
You can configure the mandatory attributes that are essential for application functionalities. That is, when a user logs in, the user information linked to these attributes are required to be shared with the application.
If the user does not have this information entered in the user profile, the user will be prompted to enter the information during the login flow.
From the attributes that are enabled for the application in the Attributes tab, you can expand the scopes and select the attributes that are mandatory for the application:
# How it works
Let's see how this flow works in Asgardeo.
Once you have configured the user attributes that are required for your application, Asgardeo implements the following process when a user tries to log in to your app.
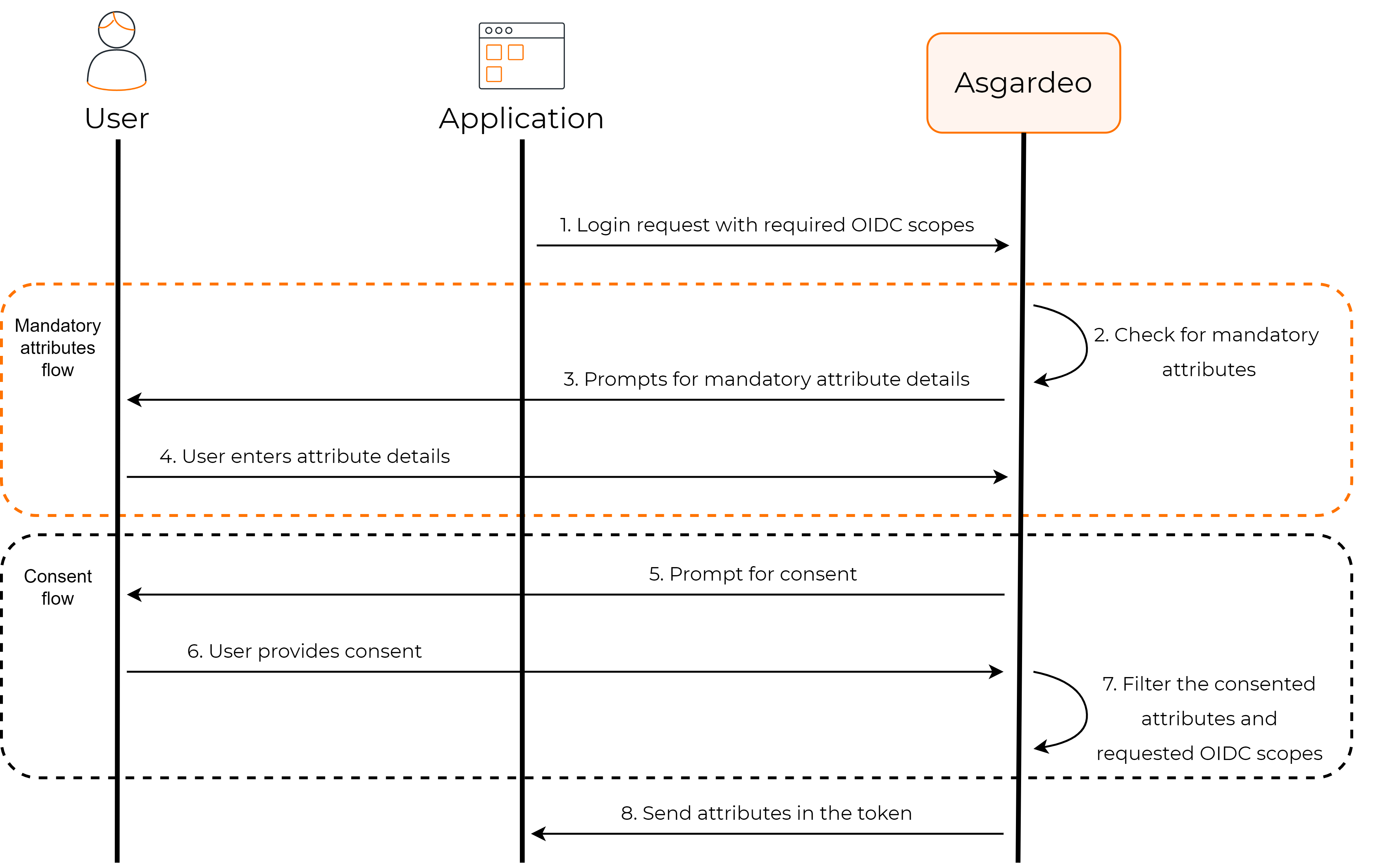
# Application requests attributes
When the user logs in to the app, a request is sent to Asgardeo with the relevant scopes.
Applications can use scopes to request access to a group of user attributes.
Learn more about managing scopes in Asgardeo.
# Asgardeo checks for mandatory attributes
Asgardeo verifies whether the user's profile has values for all the mandatory attributes that are requested by the application. If there are missing values, Asgardeo will prompt the user to enter the missing values.
# Requests user consent
By default, Asgardeo requests the user's consent to share the user attributes with the application.
Learn more about managing user consent.
# Shares attributes with the app
If the user consents to share attributes with the application, Asgardeo returns the requested user attributes as well as the subject attribute to the application in the ID token.
# Subject Attribute
The subject attribute is the unique identifer for a user. The application receives this value via the subject attribute parameter in the ID token. In Asgardeo, the user ID is used as the subject attribute.
# ID token
Once the application calls the token endpoint, Asgardeo sends the ID token in the response.
All the user attributes that are requested by scopes are returned as claims in the ID token. The application can decode the ID token to view the claims.
A sample ID token is given below:
{
"isk": "69b37037a2349763dc48e2a30a62c3feebf0b5823cf869e149352737ddc0ca63",
"at_hash": "7qgloEmkz3kGBTtH7RI4qw",
"sub": "e46ffa67-100d-4329-9460-b8251d446518",
"amr": [
"BasicAuthenticator"
],
"iss": "https://api.asgardeo.io/t/bitfrost/oauth2/token",
"given_name": "alice",
"sid": "5580be2b-a12d-43a4-823a-9d1352b88269",
"aud": "UEP40cZTZfxJfGdDWFmTrwqluxoa",
"c_hash": "VlKxb3UhuYtFEG_VftAa0g",
"nbf": 1625557031,
"azp": "UEP40cZTZfxJfGdDWFmTrwqluxoa",
"nickname": "nick",
"exp": 1625560631,
"iat": 1625557031,
"family_name": "john"
}
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# Userinfo response
In addition to getting attributes from the ID token, the application can invoke the userinfo endpoint and get user attributes along with the subject attribute.
A sample userinfo response is given below:
{
"sub": "e46ffa67-100d-4329-9460-b8251d446518",
"nickname": "nick",
"given_name": "alice",
"family_name": "john"
}
2
3
4
5
6
