CIAM: The Future of the (Digital) Enterprise - Part 2

- Sagara Gunathunga
- Head of IAM DevRel - WSO2
This is the second article in a series which discusses the rise of the digital economy, how it has become an integral part of a business’s survival today, and how Customer Identity and Access Management (CIAM) is the ideal solution to tackle challenges encountered by businesses as they implement their digital transformation strategies. The first article of this series concluded with a brief introduction to several CIAM capabilities, which are:
- Connecting with customers
- Providing personalized customer experiences
- Protecting customer data
This article will deep-dive into each of these capabilities further.
Bring Your Own Identity (BYOI)
As we discussed in the previous article, customers are overwhelmed when requested to complete several different registration forms, where they need to select usernames and passwords for the user profiles of each digital service they intend to use.
Bring Your Own Identity (BYOI) is a concept whereby customers can bring user profiles data from 3rd party services in order to create new user profile or customers can use 3rd party services for authentication ( this eliminate picking username & password per digital service problem) or they can use both options. BYOI allows users to select a number of identity sources and depending on the business context, digital service designers much use the most suitable sources. Some popular sources include:
- Social network sites such as Facebook, Twitter, Google, and LinkedIn. In this case digital services must recognize the respective social network as a trusted identity provider.
- A central identity service for digital services offered by group of companies or among business partners. Such cases require a prior agreement to use this identity service among business partners.
- Systems that have identity data as the source of identity. Mobile operators are the best example for this category. Each time a new mobile connection is purchased, the mobile operation creates a user profile which the operator authenticates through the mobile SIM whenever the connection is used. GSMA Mobile Connect is an authentication service which enables digital services (and applications) to use profiles with mobile operators as the source of identity.
- Citizen based identity services maintained by public institutions and governments agencies such as eIDs in the EU and BankId in Sweden. Digital services can use such public identity services as the trusted identity source.
Creating Customer Profiles From External Identity Services
When a new customer visits a digital application for the first time, he/she is given an option to create a new profile by completing a registration form provided by the particular application or give the option to bring his/her user profile data from external identity service trusted by the application.
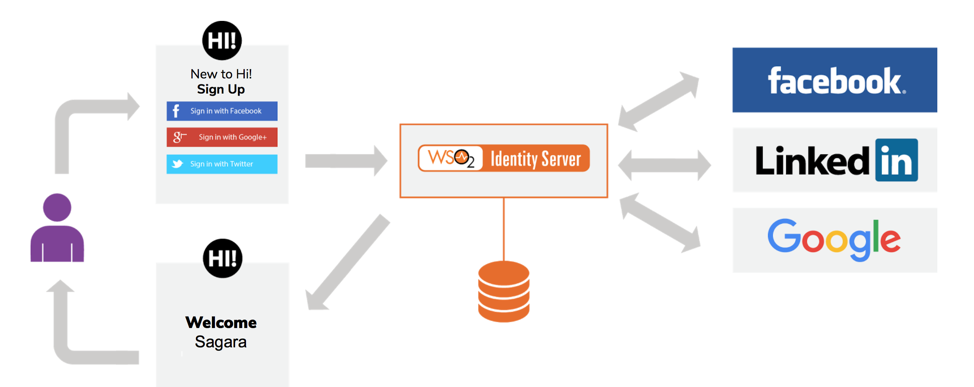
The following diagram illustrates a use case based on social networks and WSO2 Identity Server as the CIAM solution:
- A new customer named Bob visits the digital application called Deliver4U.com
- The application recognizes Bob as a new customer and gives him an option to create a user account based on any of following options:
- Bob decides to sign-up via the Facebook option
- Deliver4U.com application redirects Bob to Facebook
- Facebook authenticates Bob and requests his consent to share the user profile data stored with Facebook (i.e. name and email address) with Deliver4U.com
- Once Bob has provided his consent, Facebook securely provides Bob’s profile data toDeliver4U.com
- Deliver4U.com creates a new user account for Bob from profile data returned from Facebook and asks for any missing profile data (such as delivery address in this case)
a. Complete the registration form provided by Deliver4U.com
b. Import existing identity profile data from Facebook
c. Import existing identity profile data from LinkedIn
d. Import existing identity profile data from Google
There are two implementation options available to integrate with 3rd party services in order to import customer profiles. First, directly couple the 3rd party service with the application, in our case, Facebook SDK needs to be included as the dependency within Deliver4U.com and the same process needs to be followed with other social networks as well. As shown in the diagram above, a good CIAM solution can decouple the above dependency between applications and identity services to leverage the following advantages:
- There is no requirement to package any 3rd party service specific codes, libraries, SDKs along with the application - as long as the application supports open standards such as SAML, OpenID Connect, etc. The CIAM tool can handle 3rd party service specific logic and 3rd party service specific protocol handling.
- There is no requirement to package any 3rd party dependencies such as libraries, SDKs along with your application codes. If your application can support open standards such as OpenID Connect (OIDC), SAML then the CIAM tool can take care about connecting with 3rd party services via their own proprietary APIs a protocols.
- Adding or removing new third party services do not involve any changes in application codes. Such additions/removals are managed at the CIAM level via configurations or UI driven wizards.
- Usually CIAM vendors maintain a collection of connectors for widely used social networks and SaaS applications. As such, supporting a new social network/ SaaS application is very straightforward and it is a matter of installing a new connector at the CIAM solution level.
- Third party services may change their interfaces and SDKs. In such cases CIAM venders immediately fix their connectors to reflect those changes and the application won't require any modification to adopt changes in the 3rd party service side.
- Compared to directly coupling with a third party service option, integrating via a CIAM tool is cost and time effective. Furthermore, selecting an open source CIAM solution can eliminate vendor lock-in.
Authenticating Through Third Party Identity Service Providers
Similar to the approach we discussed in the previous section, digital applications (or services) can delegate customer authentication to a third party identity service. In such scenarios, applications only maintain the required subset of user profile data within the application storage. Password data required for customer authentication is not maintained in the application storage, instead whenever a customer is trying to log in, the customer is redirected to a third party identity service so that this service authenticates the user and returns a secure token to be used with the application.
For example, Deliver4U.com can redirect users to Facebook for authentication and trust the secure token issues by Facebook as the authentication confirmation.
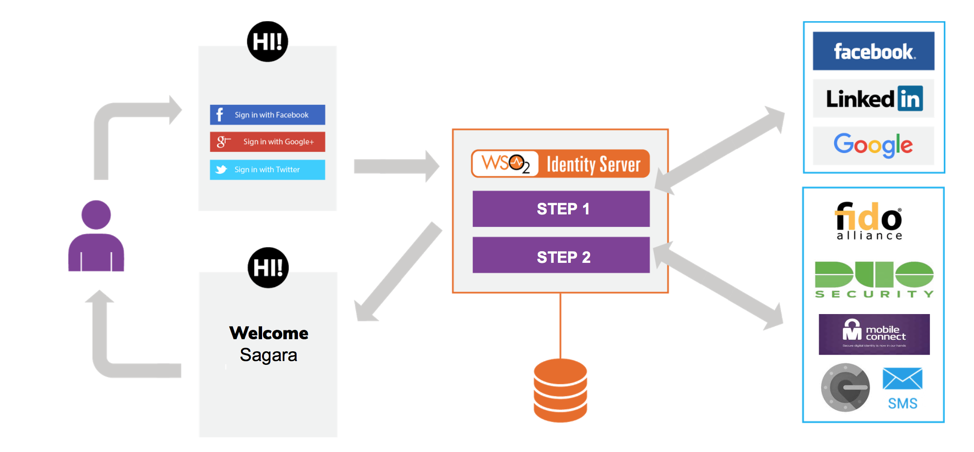
As in the previous section, application developers can directly couple with SDK provided by third party identity services or leverage the CIAM solution so that third party authentication services are fully decoupled from applications and only added, removed, modified, and/or configured at the CIAM solution level. The same set of advantages discussed in the previous section are also applicable here, in addition to the more advanced authentication options such as strong and adaptive authentication which you can achieve at the CIAM solution level.
For example, it is possible to provide authentication with multiple options or multiple steps. A user may authenticate via Facebook and then as the 2nd factor, the user can be authenticated via GSMA Mobile Connect. Such configurations are straightforward in CIAM tools are usually supported as configurations or UI wizards.
Single Sign On (SSO)
So far we have discussed how you to leverage a CIAM solution to eliminate registration and password fatigue. However, when a customer visits a set of digital applications of the same group of companies or business partners, they have to log-in each time they use a service or application (regardless of authentication happening via a 3rd party service or not). This is not the ideal user experience that we can present.
Cross-domain Single Sign On (SSO), another important feature supported by CIAM solutions, can be used to solve this problem by sharing a single logged-in session among a number of pre-agreed applications and eliminates duplicate re-logins. This will greatly improve user experiences and most session sharing instances are transparent to customers. Additionally, previously discussed authentication options such as strong authentication via multiple factors or adaptive authentication can be also used with SSO.
Progressive Profiling of customer behaviours
We discussed the importance of providing personalized user experiences in the previous article in this series. The example used was that if you are maintaining an online book store you should be able to render book suggestions based on customer behaviour such as authors of previously purchased books, subject areas of previously purchased books, based on previous search queries etc. Progressive profiling capabilities supported by CIAM tools can be used to learn these customer behaviours and adopt business logic accordingly.
This profiling can be real-time or can be offline based on large volume of historical data.
Self-care Portal for Customers
Various data we capture on user profiles such as phone numbers, email addresses, delivery addresses, and user preferences change from time to time. Hence digital applications/services should facilitate their customers to update these changes via simple and effective approaches. One solution is to build custom user profile pages with an application which involves proper design, implementation, and maintenance costs. Customer self-care portals with an available CIAM solution are ideal for such scenarios and function as a ready-made solution over customer user profile pages. These self-care portals provided by CIAM solutions do not simply act as an interface between customers and applications, but also provide data protection standards required for personal information. This is a great relief for application developers because most of these data protection standards required for personal information can be delegated to a CIAM solution.
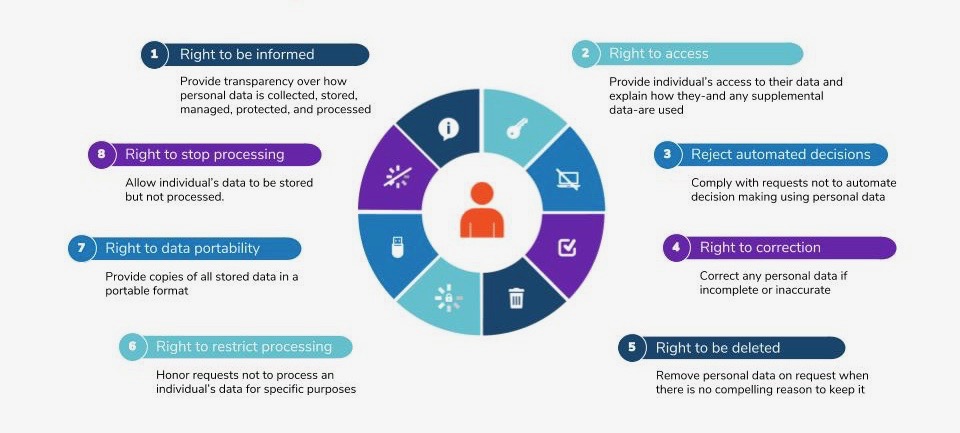
This is a very important feature due to the fact that various data protection standards are emerging all over the world. For example. the General Data Protection Regulation (GDPR) laws which came into action in May 2018 in the EU pays great attention to the protection of personal data and individual rights. In context of GDPR, self-care portals can be effectively use to review and withdraw already given consents by customers and can be used to keep user profiles up to date by the users.
Conclusion
Digital transformation is a phenomenon which has begun to influence many aspects of today’s world. Businesses that do not successfully embrace digital transformation will struggle to survive. Within this context, CIAM solutions can be one of your best companions as you begin your digital transformation journey. CIAM enables you to explore and connect with your customers digitally while providing insights on customer behavior, helping you to provide maximum privacy measures for your customers. As such, selecting the right CIAM solution must be an essential item in your digital transformation checklist.
About Author

- Sagara Gunathunga
- Head of IAM DevRel
- WSO2