Securing Your APIs with the Right API Management Solution

- Chamin Dias
- Associate Lead - Marketing - WSO2

In today’s digital business landscape, APIs have become the most important digital asset. One study found that 83% of all internet traffic belongs to API-based services. APIs act as the reusable building block that employees, partners, and customers can easily access from anywhere.
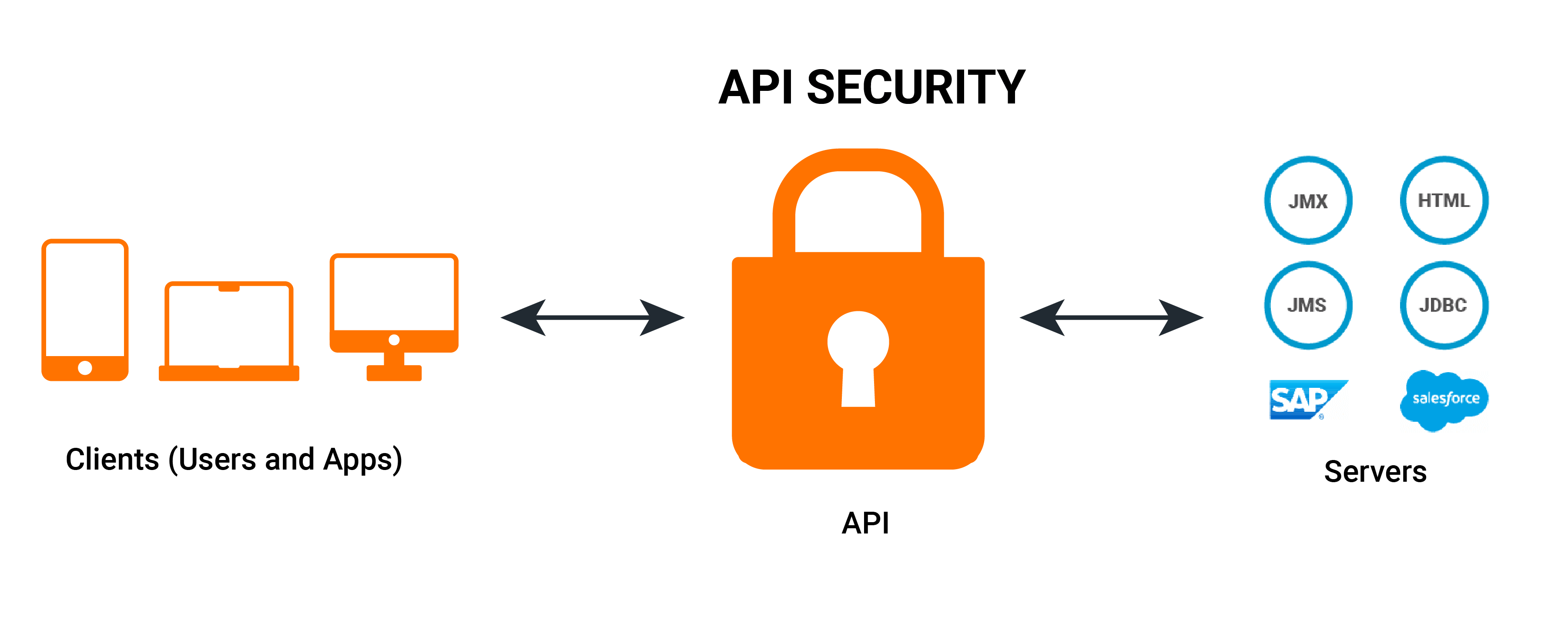
This has also made APIs the top security challenge for most companies. In a recent survey, about 94% of respondents noted that they had faced an API security issue over the past year. A single API security breach can cost millions of dollars or more.
The incident that happened in Parler (due to a security issue in public APIs), the LinkedIn scraping issue, and the attack on Microsoft Exchange Server (targeting web components and its APIs) are some of the notable API security breaches in recent history. There was another incident due to one of Clubhouse’s APIs being exposed without authentication.
How Should you Secure APIs?
Any API called by outside parties, or external APIs you call, exposes existing systems to the world. The preferred and proven approach for securing APIs is by using an API gateway. It acts as a proxy for all traffic, enforcing various policies on API traffic. There are many different implementation patterns, from a more traditional API gateway, or layers of gateways in a DMZ behind a web application firewall (WAF), to micro gateways within a service mesh running on Kubernetes. But the basic principles, and how you secure traffic, are basically the same.
In this context, the following areas should be considered.
A Strong Authentication and Authorization Mechanism
- Authentication and authorization are the heart of any API security mechanism. The system must be capable of verifying the identity of the user (to confirm who they claim to be) and only allow permitted operations to be conducted by that particular user.
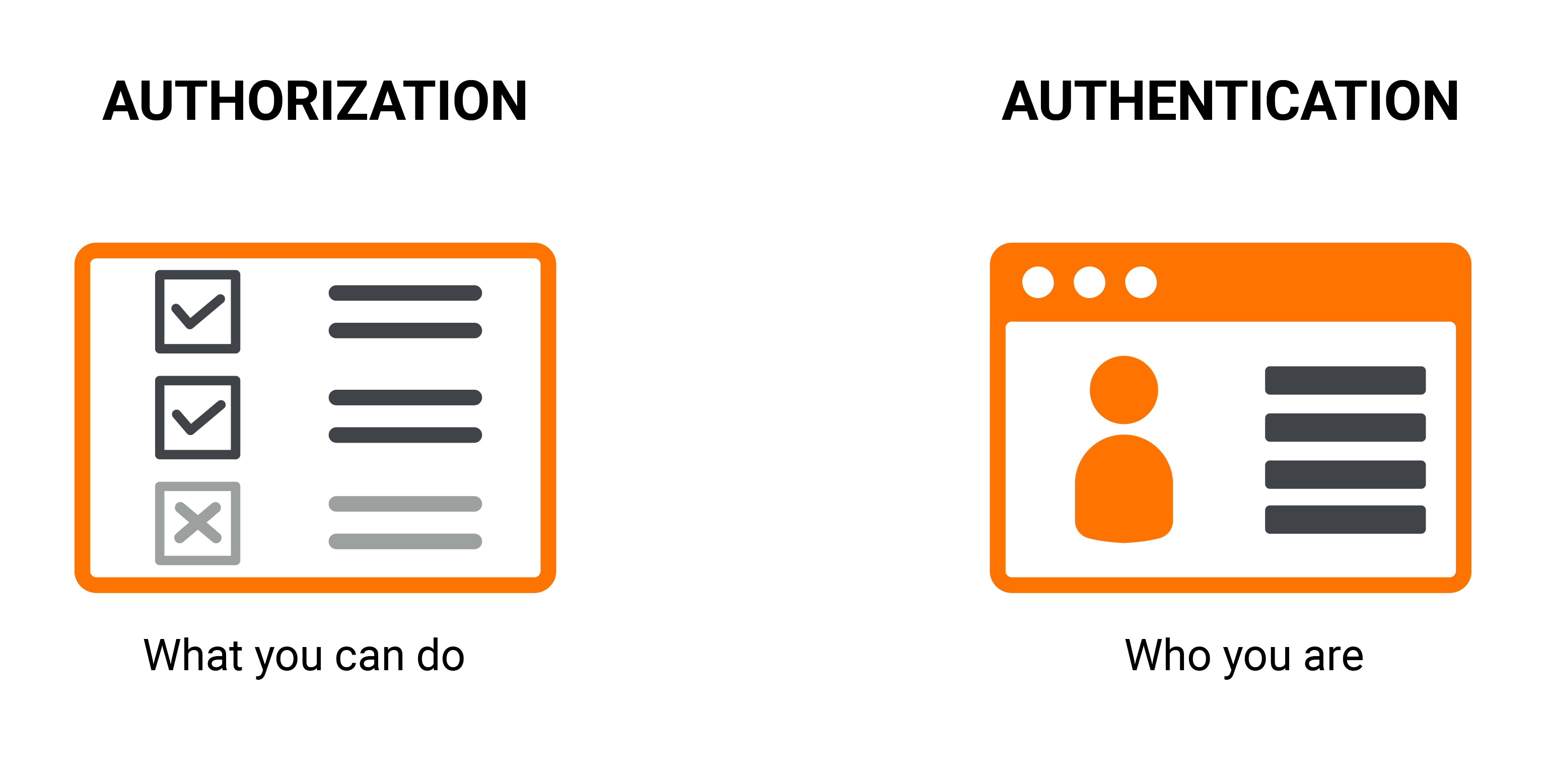
Figure 2: Authentication and authorization
Implement Fine-grained Access Control Support Integration with Other Identity Providers Detect and Prevent Fraudulent Access Monitor, Trace, and Notify in Real-time Validate all Calls It takes a considerable amount of time and effort for an organization to implement all these security measures. Also, these should be continuously updated and maintained to ensure the safety of the API ecosystem, which can amount to a significant cost and effort burden. This is where the right API management solution becomes a lifesaver. The following aspects should be considered when choosing an API management solution for an organization. At the end of the day, the implementation layer accounts for a significant part of the security mechanism. Here are 7 aspects to look at when evaluating an API management platform that offers first-class API security. 1. Developer Friendliness API developers and system engineers play a key role in designing and implementing the final API management system. To make this process productive, the API management solution should be developer-friendly so that developers have the resources to rapidly configure, test, and deploy the security controls to the chosen system. 2. Supporting Modern Protocols Since APIs have been adopted by many heterogeneous applications, there is a continuous need to support modern technologies and protocols such as Async APIs and GraphQL. This ensures that the system has the latest fixes, updates, and features, and can support multiple applications simultaneously. 3. Transport Layer Security Transport layer security (TLS) is a pivotal technical aspect of a secure API management platform. This ensures the communications and information exchanged between the client and the API stay encrypted so that potential man-in-the-middle attacks can be prevented. 4. Application and User-level Security In an API ecosystem, there might be hundreds of applications and users. End-to-end security or message-level security can be considered application-level security. User-level security restricts data or services on a need-to-know basis, mitigating the risk of a data breach. Both must be considered when evaluating API management systems. 5. Payload (or Content) Inspection When exposing an API to a consumer, the API management layer must be able to inspect the payload sent and look for any malicious content before the payload is processed by the actual service to avoid intentional or unintentional misuse. 6. Using Advanced AI Algorithms With sophisticated security attacks on APIs, AI-based security mechanisms often save a lot of time and effort when monitoring the security of the API ecosystem. When selling an API management solution, the support for AI-based security must be considered. 7. Extendability There may be situations where users aren’t showing interest in leveraging in-built security capabilities. In such cases, there should be a way to plug an external IDP. This post summarized the aspects enterprises need to address when creating a fully-secured API management solution. Keeping these in mind will help you to develop an API ecosystem that is trusted by your customers. To learn more about today’s API security challenges and how to address them properly, we encourage you to read this article. Moreover, the Total Economic Impact Study by Forrester Consulting Analysts will give you detailed information about how to quickly pursue digital initiatives to achieve sustained growth, enhanced innovation, and first-class API security.
7 Areas you Shouldn’t Ignore When Selecting a Secure API Management Solution
Conclusion
