7 Key Features of WSO2 Identity Server 7.0 Every Application and API Developer Should Know

- Sagara Gunathunga
- Head of IAM DevRel, WSO2
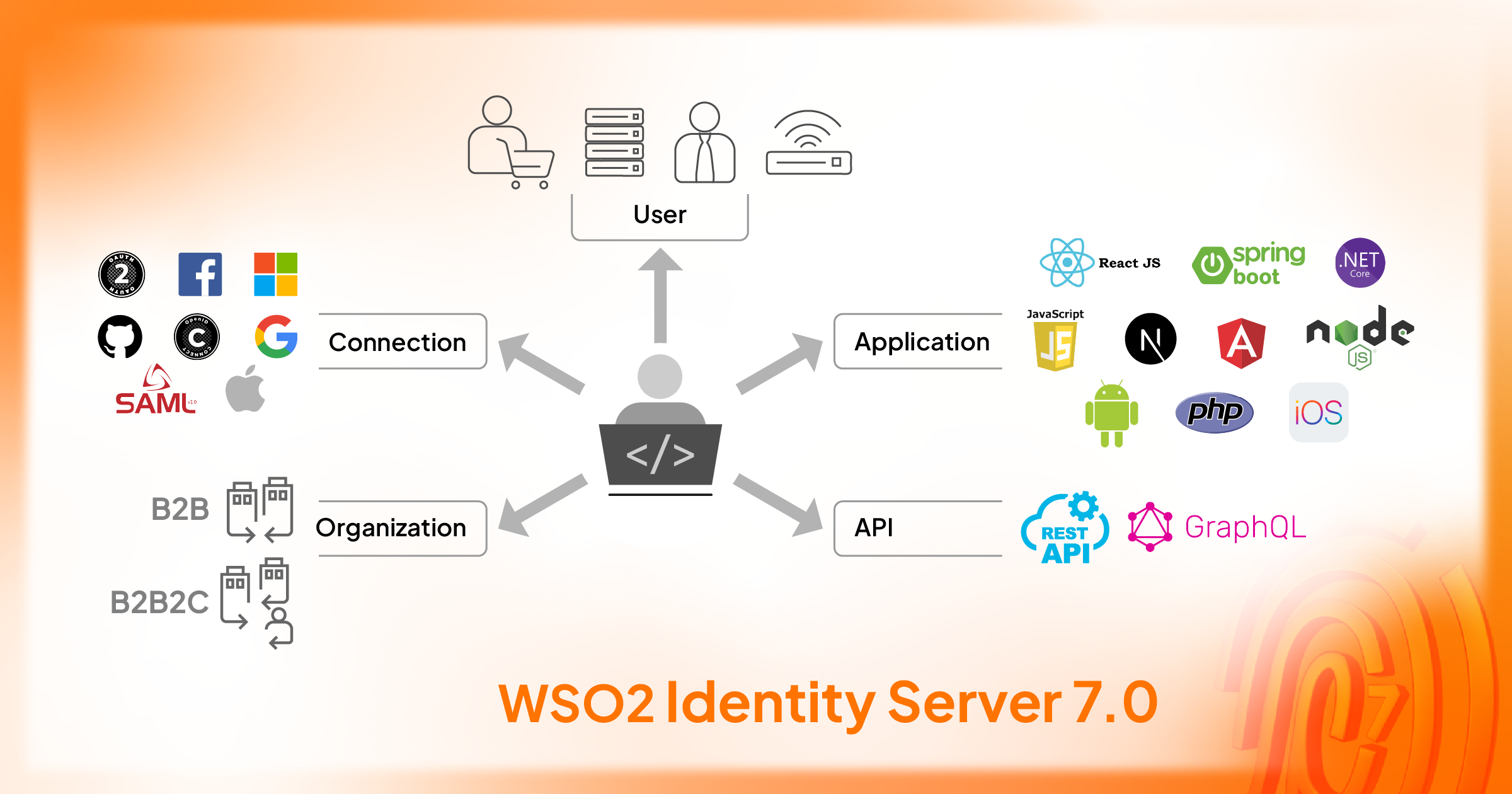
As the open source leader in IAM, we’re excited to release WSO2 Identity Server 7.0. If you’ve been involved in the IAM space for some time, you might remember that WSO2 Identity Server 5.0 released in 2014, which was a revolutionary product at that time. It brought an innovative experience for identity domain experts to model and implement their access management requirements.
WSO2 Identity Server 5.0 introduced IAM features centered around two main concepts: service providers (SP) and identity providers (IdP). The product supported the latest advancements in identity technology (at that time) like social and enterprise logins, single sign-on (SSO) for enterprise and software-as-a-service (SaaS) applications, a diverse range of multi-factor authentication (MFA) options, and user provisioning from/to cloud applications.
WSO2 Identity Server 7.0 continues our tradition of innovation and excellence, offering a brand new developer experience and advanced capabilities to meet the evolving needs of our users. While traditionally focused on IAM experts, we recognize the growing need for developer-friendly solutions. Our latest release empowers both application and API developers to easily secure their applications and APIs.
The brand-new, state-of-the-art developer console is the cornerstone of the redefined experience. The product comes with a simplified user interface, guided workflows, templates, APIs, and DevOps toolkits.
WSO2 Identity Server 7.0 also embraces the latest innovations in the IAM space and lays the foundation for AI-enabled IAM features. Notably, it becomes the first open-source IAM solution with comprehensive business-to-business (B2B) capabilities, enabling secure B2B applications through built-in user interfaces and APIs.
In this post, I'm introducing some of the product’s key innovative features and how they deliver a developer-centric experience and meet evolving user requirements.
1. Brand New Application Developer Experience

Traditionally, IAM solutions were designed to cater to the needs of identity domain experts, including identity architects, user administrators, and security architects. However, some IAM technical areas are beginning to overlap with application development owing to the rise of simple identity standards (like OAuth2, OpenID Connect) and ever-increasing security threats.
Expertise in core IAM concepts (like authentication, authorization, and user provisioning) and familiarity with open standards (like OAuth2, OpenID Connect, SAML 2.0, and SCIM 2.0) are now becoming common expectations from a typical application developer. To acknowledge this paradigm shift, WSO2 Identity Server 7.0 introduces a brand-new developer experience tailored for application and API developers, emphasizing simplicity and intuitiveness.
When developers log in to the brand-new console, they can quickly understand what needs to be done to secure the applications according to business requirements. And they can easily map the terminology used in business use cases to the components in the new console without translating these into IAM-specific jargon.

The landscape for application development is inherently heterogeneous and complex. There are a wide array of programming languages and frameworks to choose from, and the requirements of a typical web application differ from those of a single-page application (SPA) or a native mobile application. When securing an application, it's necessary to consider all these complexities.
For example, traditional server-side web applications may authenticate themselves with the identity solution during token requests, which is known as client authentication in OAuth2, but this approach is not recommended for single-page applications (SPAs). Instead, SPAs are required to use secure extensions like proof key of code exchange (PKCE). It's not easy for a typical application and API developer to identify and implement recommended best practices for securing various types of applications.
To address this challenge, WSO2 Identity Server 7.0 offers built-in application templates. These templates enable developers to easily select the appropriate template for their type of application or API. The application templates ensure that applications are configured and applied according to security best practices. Configuration parameters that are not recommended for a particular application type are disabled by default to prevent unintended security misconfigurations. Moreover, protocol-specific generic templates like security assertion markup language (SAML) and OpenID Connect are available for experienced developers to address complex application security requirements.

When integrating an application with an identity provider like WSO2 Identity Server, it’s essential to utilize an identity standard such as OpenID Connect or SAML 2.0. For instance, during a login attempt, an application must generate an OpenID Connect request and redirect the user, along with the request, to the identity provider. Once the authentication process is finalized, the application receives a security token from the identity provider, which it must process to establish the user's context at the application level. Similarly, when a user logs out, the application should create a logout request and send it to the identity provider, repeating a process similar to the login.
Implementing these flows and handling message processing requires developers to select the appropriate third-party framework and learn its usage thoroughly, which can be a cumbersome and time-consuming task. To overcome this, WSO2 Identity Server 7.0 offers a suite of software development kits (SDKs) to be included into applications. These SDKs are crafted to adhere to security best practices and follow the conventions of the underlying framework or language. They abstract away most of the protocol-specific processing from developers, only necessitating the configuration of required parameters. WSO2 consistently enhances and addresses any issues in these SDKs, enabling developers to seamlessly upgrade to new versions without worrying about maintenance. Moreover, these SDKs are accompanied by user guides and quick-start samples, serving as a solid foundation for real-world application development.
Considering that some identity technologies are mature, certain application development frameworks like Spring framework for Java and .Net Core framework support identity protocol handling at the framework level without external dependencies. In such cases, WSO2 provides comprehensive guides and quick-start samples that demonstrate how to leverage the features of the underlying framework to integrate WSO2 Identity Server with the application.
2. Flexible User Onboarding
Once an application is integrated with an identity provider, the next step is to onboard users. In many cases, organizations may already have user profiles maintained in systems like Active Directory, lightweight directory access protocol (LDAP), or a simple database table. WSO2 Identity Server offers built-in connectors for Active Directory and LDAP, enabling seamless integration with existing servers. Once connected, user profiles, groups, and roles become visible in WSO2 Identity Server’s console and can be utilized within integrated applications and APIs.
If a simple database is used as the existing user store, WSO2 Identity Server provides a stable extension point to connect custom user profile tables via an extension. New users can be directly onboarded to WSO2 Identity Server using the fully rebrandable login and signup portal, or applications can utilize user management APIs behind the scenes. Alternatively, existing solutions can be used to onboard users and sync with WSO2 Identity Server via the SCIM 2.0 API (this is a common pattern in employee identity use cases).
Once users are onboarded with WSO2 Identity Server, account management features are automatically enabled for these profiles out of the box. Here are some key account management features.
- User onboarding via invitations, self-registration. Invite new users and bulk user imports & exports, just-in time (JIT) in-bound and out-bound provisioning.
- Account confirmation methods for self-registration and user attributes verification.
- Account locking capabilities that includes admin-initiated locking, locking by failed login attempts, locking by failed OTP attempts.
- Account association.
- Account recovery including username recovery, reset forgotten passwords, password recovery via challenge questions, and password recovery via user-preferred notification channel.
- Notifications for user operations.

With the emergence of privacy standards such as GDPR and CCPA, organizations are required to collect clear user consent for storing user profiles. Additionally, they must facilitate users to review and modify their profiles, as well as review and revoke previously given consents. WSO2 Identity Server addresses these requirements by eliminating the need for applications to implement these features themselves.
The Self-Care User Portal is designed to offer security, user profiles, and consent management for users onboarded into WSO2 Identity Server. It serves as a separate portal, fully customizable and brandable according to your needs. Furthermore, the Self-Care User Portal is supported by a straightforward RESTful API. This allows applications to implement user interfaces for profile and consent management by making calls to the Self-Care RESTful API, thus offering flexibility in integrating these functionalities within your application's environment
3. Multi-Factor Authentication (MFA), Passwordless, and Social Logins
Multi-factor authentication (MFA) is now a common recommendation over single-factor authentication due to its enhanced security. Passwordless authentication is also gaining widespread adoption, addressing issues related to password management. Moreover, with the integration of AI into various aspects of daily life, a range of new AI-powered authentication methods are emerging. Additionally, there is a growing demand to onboard users from social and enterprise platforms and enable login through social accounts.
To address these requirements, WSO2 Identity Server 7.0 introduces the concept of connections. Connections serve as links to external identity providers (IdPs), including both social and enterprise providers such as Google, Microsoft, Facebook, or any standard-based identity providers from business partners. These connections can also be utilized to integrate multi-factor authentication providers, like SMS and email-based OTPs, TOTPs, FIDO, and biometric authentication providers. This comprehensive approach ensures that applications integrated with WSO2 Identity Server can leverage a diverse range of authentication mechanisms and seamlessly onboard users from various platforms.
WSO2 Identity Server 7.0 introduces connection templates, akin to application templates, to streamline the integration process with external identity providers and multi-factor authentication providers. These templates are designed to simplify the integration effort for developers.

Each connection template offers a tailored user interface specific to the external identity provider being integrated. It prompts developers to configure only the necessary parameters, with pre-configured default values aligned with the expectations of the respective external identity provider. Additionally, the templates highlight the parameter values that require configuration in the external identity provider side, such as callback URLs. Each template includes links to relevant documentation pages from external identity providers, aiding developers in the integration process. WSO2 Identity Server 7.0 also provides SAML2 and OpenID Connect standard-based templates, facilitating integration with supported identity providers from business partners.
4. Visual Login Flow Editor - What You See Is What You Get
Modern applications have evolved beyond simple login pages generated by the application itself. In contemporary applications, the login page is typically generated by an identity provider and can involve multiple options and steps. For example, an application may offer users the choice to log in using their username and password, Google credentials, or Facebook as the first option. If successful, the user may then select TOTP or SMS-based OTP as the second-factor authentication.
While identity solutions offer developers the flexibility to design complex login journeys like the one described above, envisioning the actual login user interface experience can be challenging when working with traditional editors. With the release of WSO2 Identity Server 7.0, this limitation has been addressed with the introduction of a brand new Visual Login Flow Editor. This editor provides developers with a "what you see is what you get" (WYSIWYG) experience.

The new Visual Login Flow Editor significantly reduces development time by enabling developers to visually arrange and configure the login options in the desired sequence without needing to run the application for validation. This ensures a more efficient workflow and makes it easier for developers to select the appropriate login options and arrange them logically within the flow.
5. B2B Organization Management
Traditional business models primarily involve catering directly to customers (B2C) or to other business organizations (B2B), which, in fact, act as customers themselves. In contrast, a new business model, called business-to-business-to-consumer (B2B2C), has emerged in recent years. In this model, a business provides its products or services to the customers of another business via that business. In this case the other business is acting as an intermediary, serving as a bridge between the original business and the end-user. The intermediary business may add value through marketing, sales, or other services to enhance the overall customer experience.
The B2B2C model is gaining popularity in industries such as technology, insurance, and retail, where partnerships and collaborations enable companies to reach a broader audience and leverage each other's strengths. To accommodate the requirements of both B2B and B2B2C businesses, the application architecture must evolve. In addition to targeting direct customers, consumer applications must facilitate the onboarding of business organizations and their users. They should allow staff members of onboarded organizations to handle administrative tasks and, most importantly, enable customers from those onboarded organizations to access the business capabilities seamlessly. Needless to say, identity architecture and solutions must also evolve and work hand in hand with the application architecture to build successful B2B and B2B2C business applications.
With the release of version 7.0, WSO2 Identity Server becomes the very first open-source IAM solution to provide a complete and comprehensive set of capabilities for building applications to serve B2C, B2B, and B2B2C models. WSO2 Identity Server 7.0 introduces a new first-class concept called "organization" to represent other businesses and facilitates the onboarding and management of these other business organizations through modern user interfaces or via RESTful APIs, which can be integrated with separate CRM systems. Additionally, WSO2 Identity Server 7.0 further facilitates the onboarding of administrative staff from other businesses, enabling them to onboard their customers by connecting their own identity providers and customizing the application according to their branding policies. Once an application is shared with another business organization, their customers can log in to the application through the identity provider of that particular business organization, providing a frictionless login experience and eliminating duplicate signup processes.
Some key B2B organization management features includes:
- Simplified onboarding of business organizations via invitations and self-sign up.
- Delegated administration.
- BYO identity providers for on-boraded business organizations.
- Customized login flows for shared applications.
- Role-based access control.
- Customized branding.
- Flexibility to adapt to any organizational structure and scale.
6. Frictionless App-Native Authentication
Redirecting users to the identity provider for login and rendering the login screen at the identity provider level works well for both server-side and browser-based applications. Modern identity solutions allow for rebranding the login screen to match your application's branding, resulting in a seamless login journey for users.
However, for native applications developed on platforms like Apple or Android, using the system browser to redirect users to the identity provider can introduce friction in the login journey. While this approach is secure, it's not always ideal from a user experience standpoint. Native application developers have raised concerns about this friction.
To address this limitation, WSO2 Identity Server 7.0 introduces a new API-based authentication approach. With this approach, the login screen is rendered entirely within the native application using APIs provided by the Identity Server. This enables native application developers to deliver a frictionless login experience to users, improving overall usability.
We're excited to launch this highly requested feature that will make it easier to deliver frictionless login experiences. Early adopters are already eager to give it a try!

7. The Brand New API Developer Experience
API security has long been recognized as a critical aspect of identity provider functionality, with virtually every IAM solution supporting it. Typically, identity providers manage API security through security token service (STS) capabilities, which involve issuing, validating, and revoking security tokens for API access.
However, identity providers have historically lacked the capability to treat APIs as first-class citizens, limiting the ability of API developers to register their APIs, define resources, associate permissions with each resource, and establish authorization policies for token issuance. Fortunately, this trend is beginning to change.
With the latest release, WSO2 Identity Server is embracing this industry shift by allowing API developers to represent API resources as first-class citizens within its brand-new console. Once an API is registered, developers can define and associate a set of permissions in the form of scopes. These API resources and associated scopes can then be used to define authorization policies, ensuring that authorization policies are evaluated before issuing an access token.

Currently, authorization policies are based on the built-in role-based access control (RBAC) module, providing a comprehensive framework for managing access control policies within the identity provider.
OAuth2 and OpenID Connect standards offer a wide range of choices to accommodate diverse applications and APIs across various industries. However, this flexibility can present challenges for average API developers who may struggle to select the appropriate options for their APIs. For instance, determining the suitable client authentication mechanism or cryptographic key size can be daunting.
To address this challenge, the FAPI working group, under the OpenID Foundation, has developed a series of specifications such as FAPI 1.0 Baseline, FAPI 1.0 Advanced, and FAPI 2.0. These specifications provide clear guidelines for API developers to follow based on their security requirements. For example, FAPI 1.0 Baseline specifies that identity providers should support Mutual TLS, client_secret_jwt and private_key_jwt methods for the client authentication and define the minimum key size of 2048 bits for RSA algorithms and 160 bits for elliptic curve algorithms.
By adhering to these specifications, API developers can easily configure the security parameters of their APIs. WSO2 Identity Server 7.0 further simplifies FAPI compliance by introducing an option for developers to specify FAPI compliance requirements. Then, WSO2 Identity Server automatically configures security parameters according to the FAPI specification, streamlining the process for API developers
Summary
WSO2 Identity Server 7.0 introduces several key features that are essential for application and API developers. It offers a brand-new developer experience tailored specifically for application and API developers, simplifying the process of securing applications and APIs. The platform provides built-in application templates, SDKs, and comprehensive guides to streamline integration efforts and ensure adherence to security best practices. Additionally, WSO2 Identity Server 7.0 introduces flexible user onboarding capabilities, supporting seamless integration with existing user stores and offering account management features out-of-the-box. Furthermore, the platform enhances authentication mechanisms with multi-factor authentication, passwordless authentication, and social logins, catering to modern security requirements. It also introduces a visual login flow editor for easier customization of login journeys. Moreover, the API developer experience has been enhanced with first-class support for API resources, scopes, and authorization policies. The product also introduces B2B organization management features, enabling organizations to onboard and manage other businesses and their users seamlessly. Overall, these features empower application and API developers to build secure, user-friendly, and scalable solutions effectively.
Learn more about WSO2 Identity Server 7.0 and explore its features by visiting https://wso2.com/identity-server/.

