Behavioral Authentication: Improving Security and CX Without Compromise
- Seshika Fernando
- Vice President - Banking and Financial Services - WSO2
- 21 Jun, 2023
Key Takeaways
- Present day user-driven authentication mechanisms have forced banks to treat security and customer experience (CX) as two ends of a see-saw — resulting in a clunky and less desirable customer experience.
- Data-driven behavioral authentication (DBA) is a promising solution that relies on automated identity verification using the large amounts of customer data already captured through the banking process, instead of interrupting a user for multiple verifications.
- DBA enables banks to simultaneously tighten security and improve CX, making it a mutually reinforcing process.
Introduction
Whether it’s movie recommendations from Netflix or suggested workouts from Apple Fitness, consumers expect ultra-personalized digital services everywhere, including their banks. However, the extremely high demands to protect customers’ finances from fraud and theft have left most banks unable to rise to consumers’ expectations.
Contributing to the challenge has been a reliance on user-driven customer identity and access management (CIAM) systems that require customers to provide information each time verification is needed – not just to logon but also for many banking transactions.
Fortunately, the emergence of CIAM solutions that support data-driven behavioral authentication (DBA) offers the potential for banks to provide the seamless, personalized experiences consumers expect. DBA automatically verifies customers behind the scenes and without interrupting the user by using large amounts of data already captured through banking processes.
This paper examines how adopting data-driven behavioral authentication can transform the security vs. CX see-saw into a mutually reinforcing virtuous cycle where digital banking experiences not only drive customers’ loyalty but also achieve stronger security to ensure their trust.
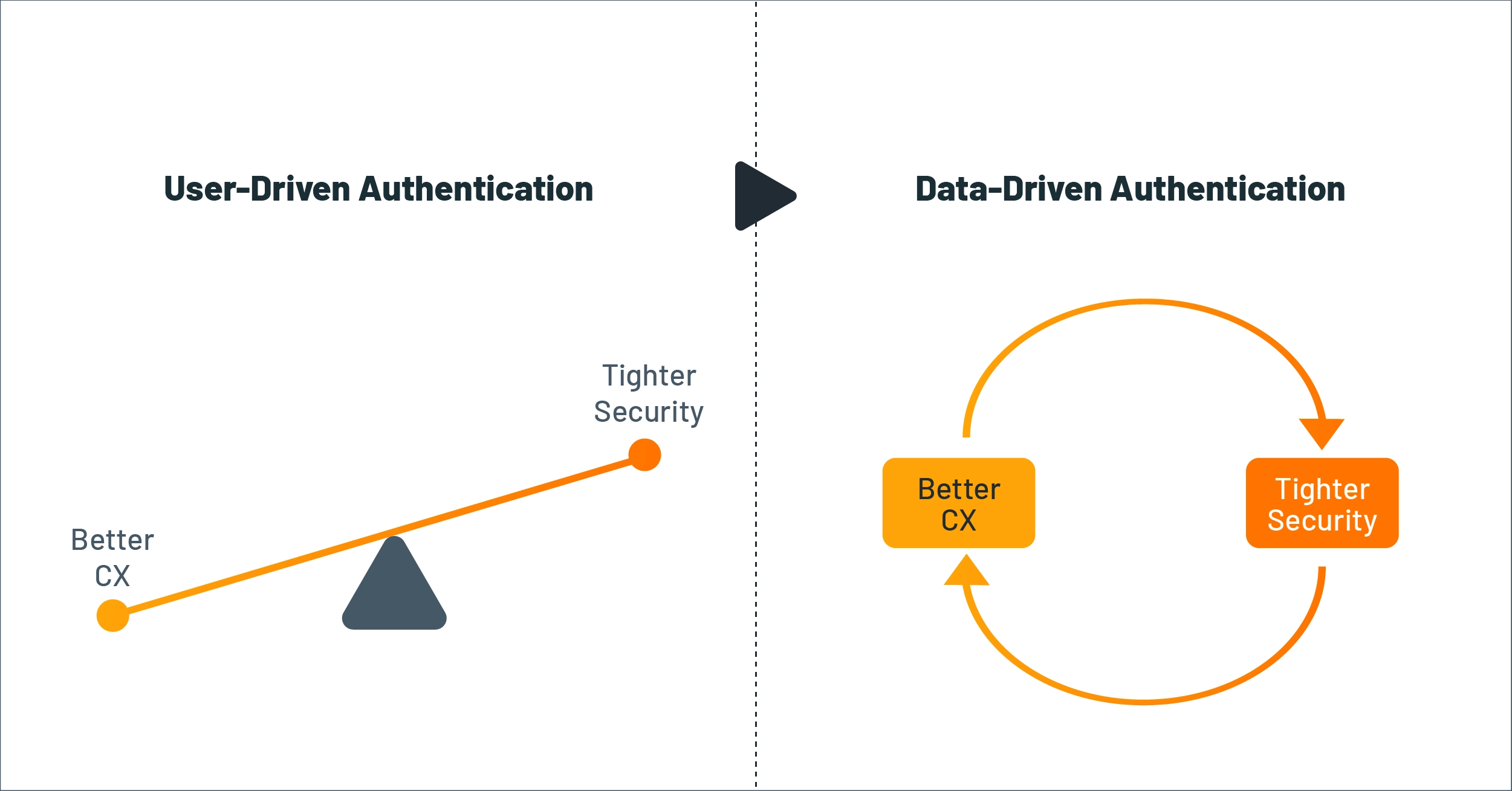
Figure 1: DBA enhances security and CX
The Crux of the Matter: User-Driven Authentication
Banks must maintain customer authenticity and intent throughout digital banking sessions, not just at the initial logon. However, current CIAM systems provide user-driven authentication mechanisms that depend on user-submitted data for each verification. This can interrupt customers several times within a single session, making the experience clunky and leaving users feeling like they’re not trusted. On the other hand, banks that don’t take this precaution may expose customers to worse outcomes than annoying interruptions.
User-Driven Authentication Takes Many Forms
Beyond using a basic username/password combination, banks often use multi-factor authentication (MFA) to perform more comprehensive checks on customer authenticity and intent. As shown below, this requires customers to submit different types of information at various verification points during their digital interactions.
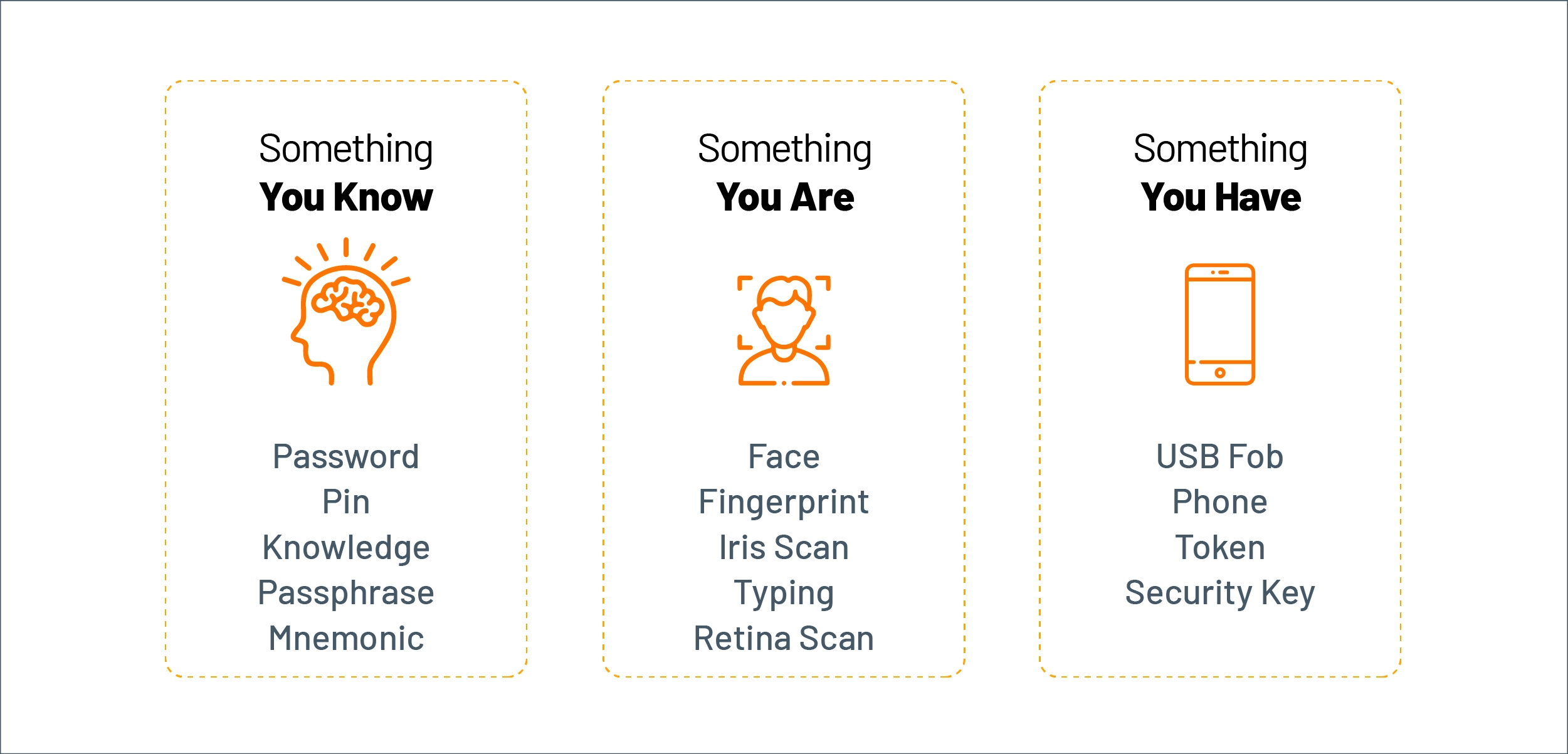
Figure 2: Factors used in multi-factor authentication
While MFA was popular a few years ago, it has now become a nuisance for customers. This is particularly true during digital banking sessions, where the need to provide additional verification information before certain financial transactions can lead to frequent interruptions.
How User-Driven Authentication Impacts CX
Today, banks and other financial institutions often have to strike a less-than-ideal balance, as the graphic below illustrates. Most banks tend to focus on security, resulting in a clunky and less-than-desirable customer experience. Meanwhile, at banks where security teams are more pro-CX, the enterprise architecture or authentication technology does not provide the ability to make use of identity data across systems through APIs, which ironically limits the potential to use identity data for a better customer experience.
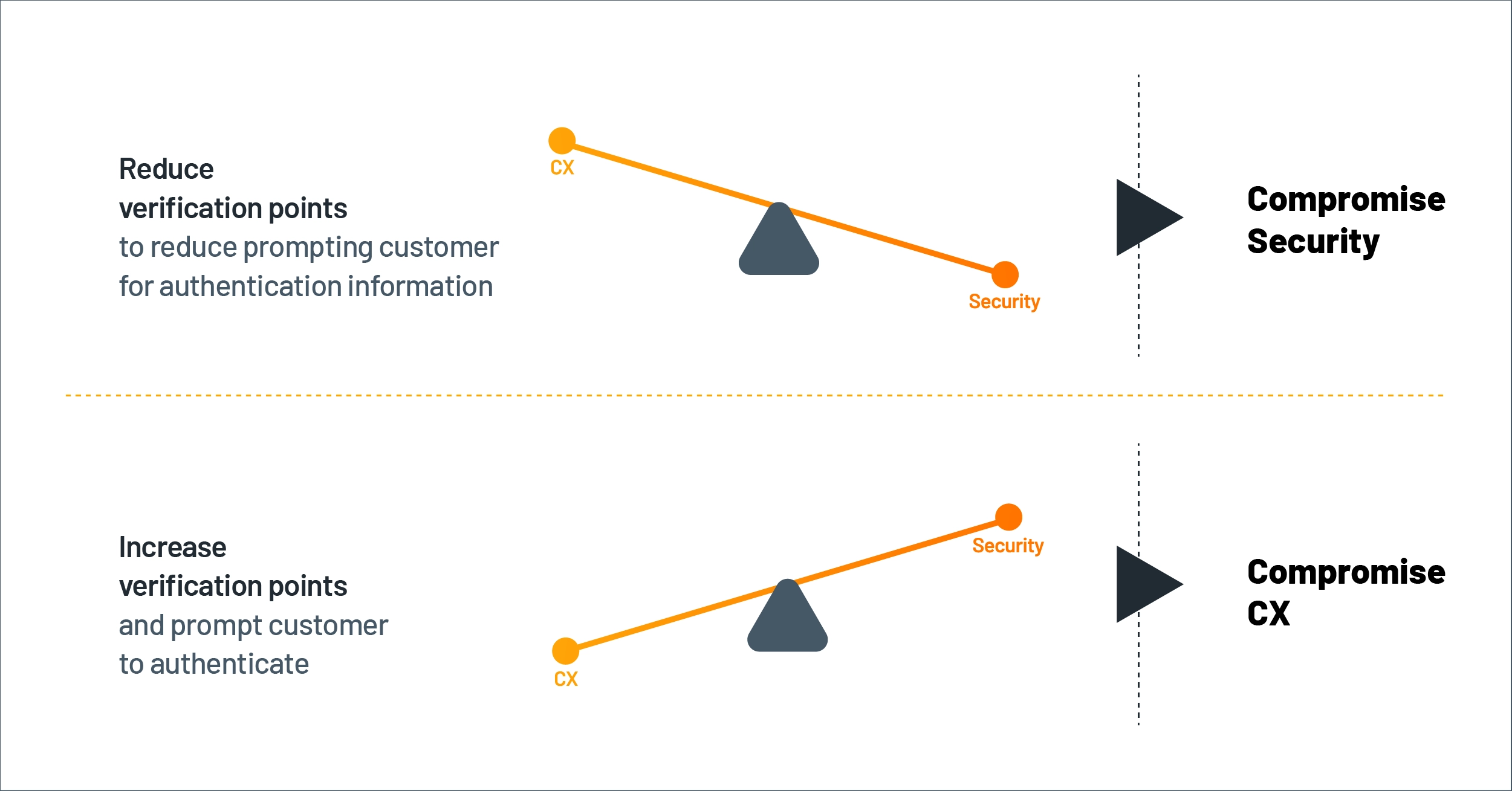
Figure 3: Balancing security and CX
Some banks have tried to reduce the friction caused by user-driven authentication by introducing biometric verification, but that doesn’t solve the problem completely because it still requires a specific action from the consumer. Moreover, it is only available to users with access to biometric technology.
In a recent discussion, OTP Bank Romania’s Chief Digital Officer Constantin Mares observed that “replacing the existing authentication factors with biometrics has improved the customer journey significantly, but we would prefer to improve it further, especially to adopt more data-driven authentication.”
Introducing Data-Driven Behavioral Authentication
Data-driven behavioral authentication frees banks from having to maintain this delicate balance since it enables a bank to simultaneously tighten security and improve CX.
DBA relies on verifications that are performed automatically by utilizing the large amounts of customer data already captured through the banking process instead of prompting users to verify themselves."
Verification happens while the customer is digitally engaging with the bank, but as a background process so that the customer continues to consume financial services without frequent interruptions. The diagram below shows a high-level view of how this is done.
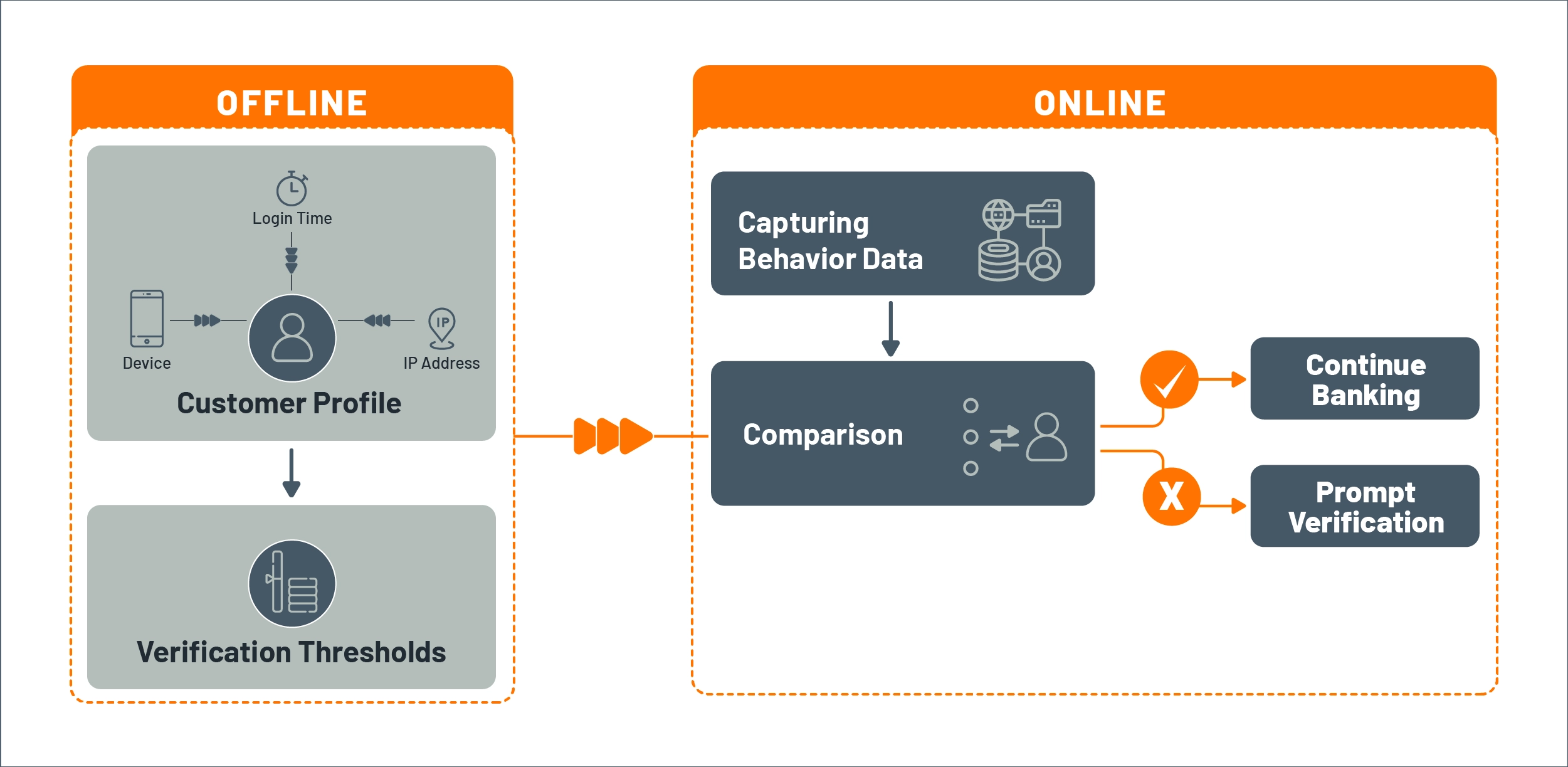
Figure 4: How DBA works
Here is an example of a customer journey with data-driven authentication.
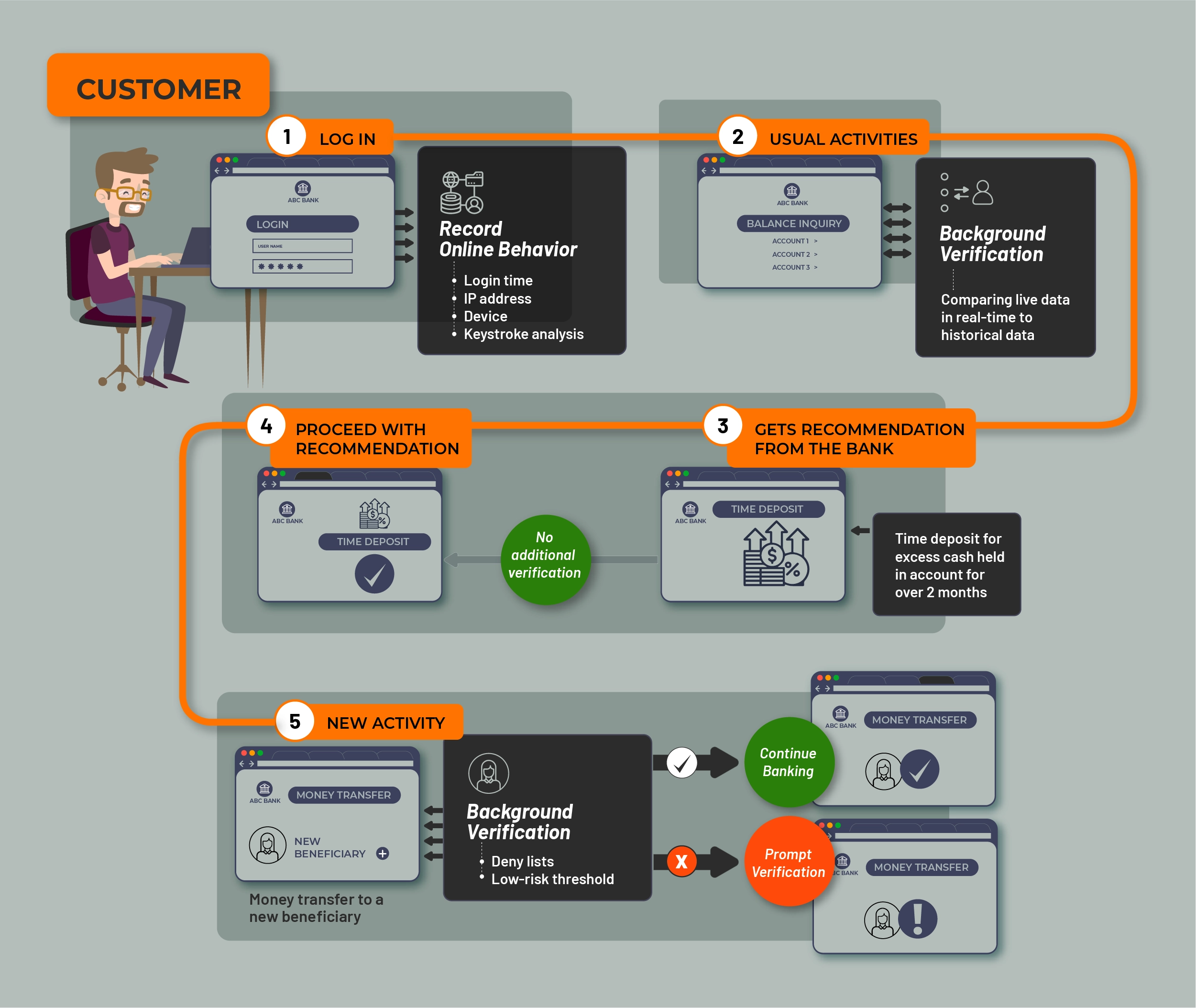
Figure 5: Example customer journey with DBA
Unlike traditional CIAM technology, the data-driven CIAM used for behavioral authentication also provides the ability to expose identity data as APIs that can be used for personalization via artificial intelligence (AI) and machine-learning (ML) technology.
Additionally, behavioral authentication using data-driven CIAM allows more comprehensive verifications to be done with increasing frequency as it uses large sets of data, and the verifications occur automatically in the background, unlike point verifications that can be performed only at certain stages of the engagement. This results in improved security and a better customer experience.
Driving Collaborative Innovation
Behavioral authentication has the potential to bring about structural change within a bank by fostering collaboration between security and product teams. With data-driven behavioral authentication, these teams no longer need to work independently or in opposite directions. Instead, they can work together on innovative products and services that improve both the customer experience and security simultaneously.
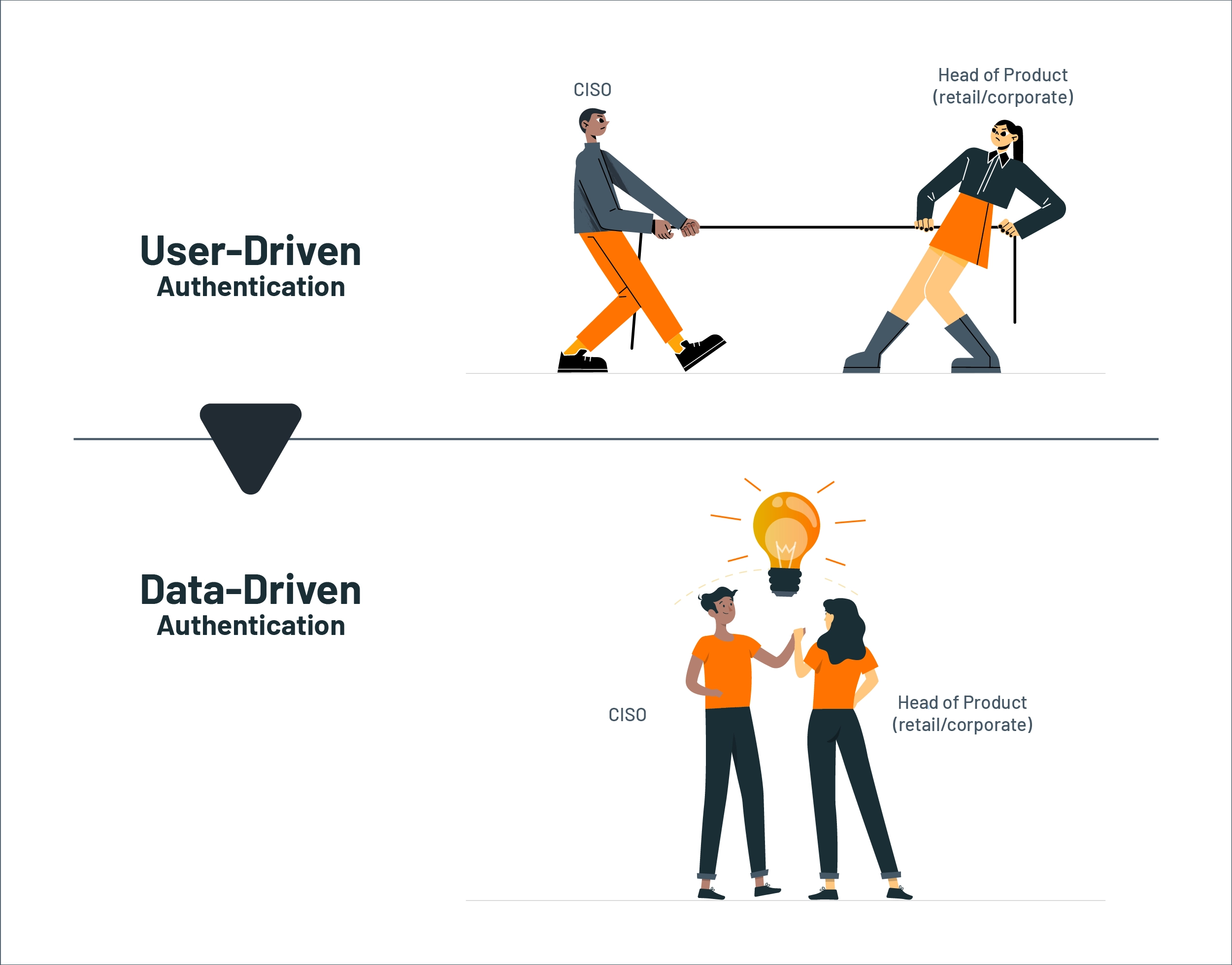
Figure 6: DBA fosters collaboration between security and product teams
How Data-Driven Authentication Works
What Data Is Captured?
Five categories of information are typically utilized for data-driven authentication. As shown in the diagram below, these include identification, usage, behavioral, demographics, and life events.
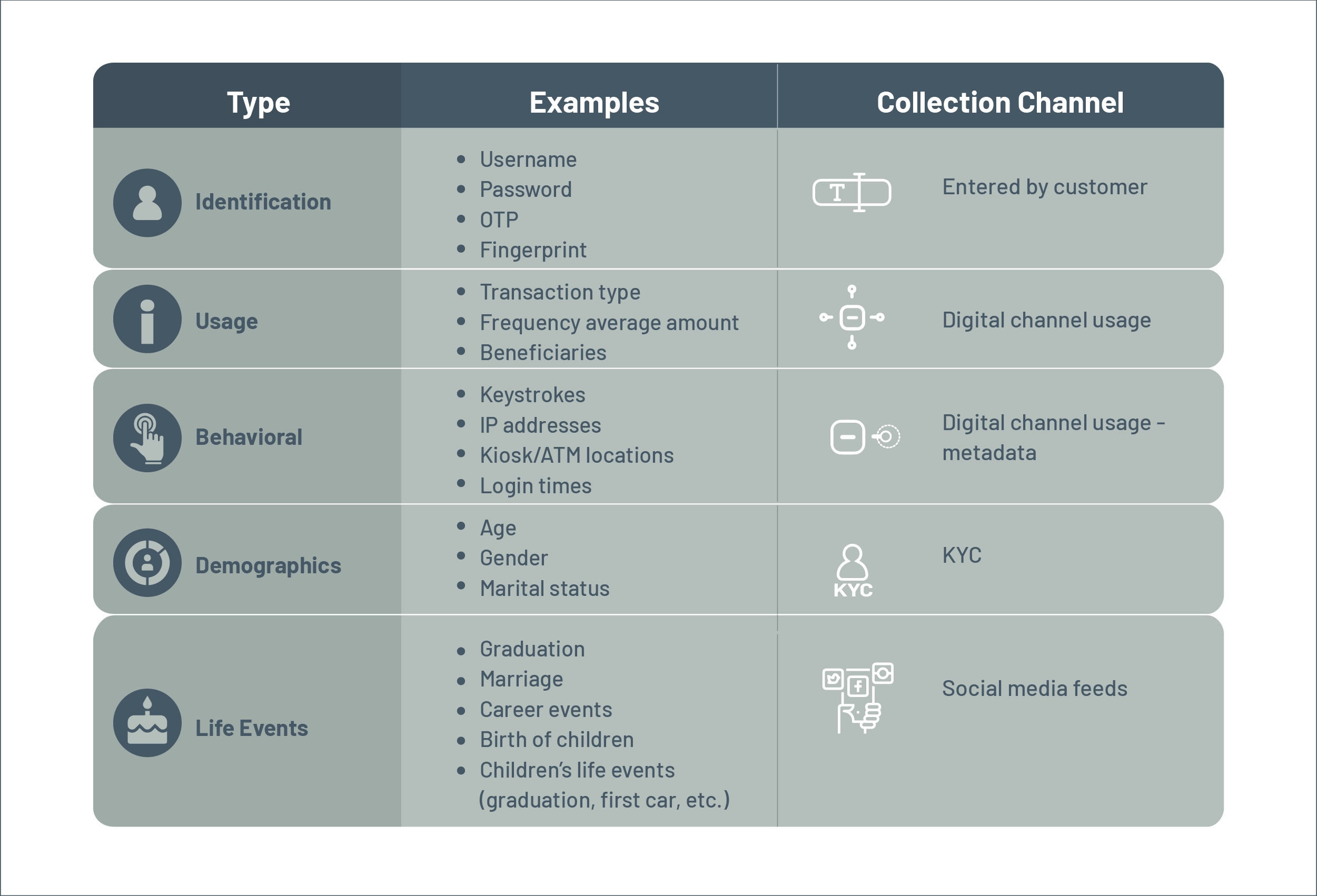
Figure 7: Five categories of information in DBA
Verification Methods
There are three primary forms of verification applied to the data collected: combination scoring, threshold setting, and machine-learning. Let’s review each method.
Combination scoring
First, verification is conducted by checking a combination of factors prior to each action instead of relying on a single indicator. Let’s take the earlier example of transferring funds to a new recipient.
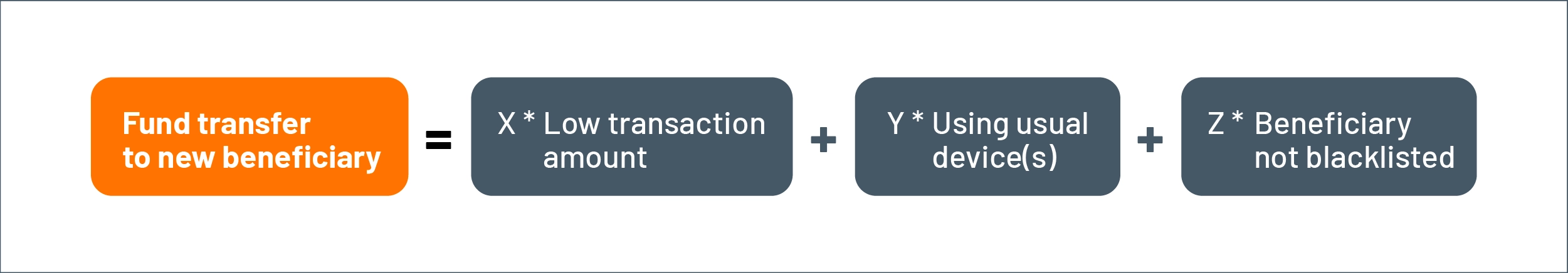
Figure 8: Combination scoring for verification
Each of these factors will have different priorities, as represented by the different weights assigned to each of them in calculating the combined risk. For example, the beneficiary check will have a higher priority than the device used to make the transaction.
Threshold setting
The final combined score is validated against different thresholds that will enable the system to react accordingly.
- Allow the transaction to be processed.
- Get an additional verification from the customer.
- Notify the customer of potential fraud.
These thresholds are inferred using historical averages. However, they can be further adjusted by the customer if they prefer an alternative to the system-generated value.
Machine learning
Combination scoring and threshold setting are sufficient for implementing verification based on known risk factors. However, machine learning is required for true behavioral authentication since ML models make it possible to validate against complex sequence patterns. In particular, Markov Models are used in dissecting a customer’s behavior into a series of actions and verifying whether the online behavior is normal or abnormal based on the customer’s historical behavior patterns.
An example of machine learning-based behavioral authentication is TypingDNA, as highlighted by Chris Skinner. He explains, "Going back a few years, there was the idea of using behavioral keyboard authentication—by the way you type and the weight of your thumbs on your keyboard—it's behavioral, and it can recognize whether it is really you. This type of authentication is far better because it provides a seamless customer experience rather than the inconvenient password or gateway authentication."
Verification Frequency
Verifications can be performed periodically as well as prior to certain actions, such as a payment to a new beneficiary, an abnormally large payment to an existing beneficiary, set-up of a standing order, or the creation of a new account.
With data-driven authentication, banks have greater flexibility to perform as many verifications as needed to support their business’ risk profile, without having to interrupt the customer’s digital banking session. Only when abnormal behavior is detected will the customer be prompted for verification, increasing consumer trust and protection while keeping the system’s inner workings as invisible as possible.
Behavioral Authentication Paves the Way for Personalization
Data used to capture a customer’s online behavior often reveals more of the customer’s personality. Therefore, this data set can be used to personalize daily transactions.
Here are some examples:
- A customer performing the same transaction every month around the same time (e.g., paying rent or utilities on payday) can be prompted to create a monthly standing order.
- A customer who has had unused funds in a checking account for a long time can be prompted to transfer the money into a high-interest-earning savings account.
- A customer making payments from an interest-earning savings account while there are sufficient funds in a checking account can be prompted to utilize the funds in the checking account without losing out on the savings account interest.
However, unlike in retail or entertainment, there is another dimension to personalizing financial products. People generally require financial products based on life events, too.
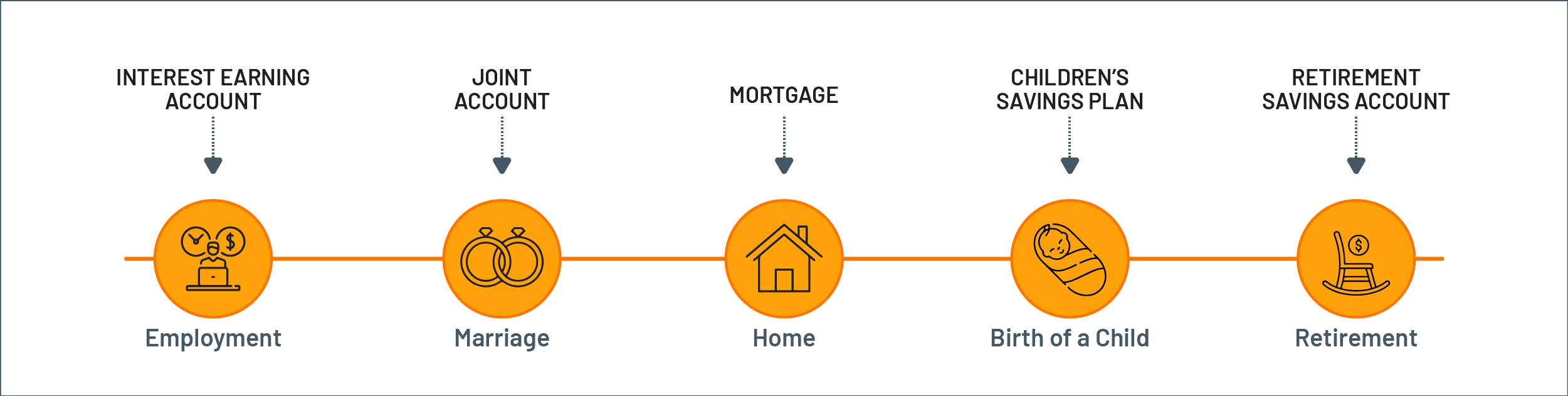
Figure 9: Personalizing financial products
This information, unfortunately, cannot be captured by just collecting data on the customer’s digital banking usage. Instead, the data is usually available elsewhere, such as in social media feeds – a LinkedIn post about a new job or promotion, a Facebook post about marriage or childbirth, a tweet about recommendations for financial products, etc.
If banks had access to this data, they could proactively provide a highly relevant and personalized experience to each of their customers. Presently, we see some progressive banks effectively showing customers the benefit of sharing some external data sources with the bank. However, this completely depends on how comfortable a customer is sharing such data, as well as the bank’s ability to handle the associated privacy and regulatory concerns in accessing a customer’s external data for personalization purposes with the utmost care.
By adhering to regulatory standards while harnessing the power of data, banks can pave the way for personalized experiences that respect customer privacy and enhance overall satisfaction.
Privacy and Consent
Banks, like any other organization, need a customer’s consent to gain access to any external data sources, such as a social media feed. Today’s consumers are generally happy to provide this consent in exchange for much more personalized and meaningful banking services.
The concept of consent is already used in open banking, where customers allow banks to share their financial data with third-parties who provide services to them based on their financial data. Generally, those customers who are willing to provide their most confidential financial data to third-parties are more likely to also share personal life information with the bank in exchange for financial services that align with their current life circumstances.
How can banks capture and maintain customer consent?
Data-driven CIAM technology provides consent management functionality. This is key to empowering customers with the required controls for sharing their external data with a bank.
Modern CIAM systems, especially ones that support open banking requirements, provide the ability to capture customer consent in a fine-grained fashion. They record which data can be shared, with whom, for how long, and for what purpose.
Additionally, CIAM systems allow customers to edit/update their consent preferences or even remove consent entirely so that data is no longer shared with a particular entity. With this type of control, customers feel more at ease consenting to share external data with their bank, as they know they can change their minds at any time.
Banks, for their part, can convince more consumers to share more external data by creating awareness of the control that a customer has over their data-sharing preferences and the compelling benefits they can gain by doing so. Banks that create this awareness through excellent CX strategies often attract more customers who appreciate having more personalized banking services.
Enabling banks to finally take advantage of open banking ecosystems
Promoting transparency about how customers control their data builds trust, helping banks become more effective at competing with fintechs, who now, in the open banking era, have access to data once exclusively held by banks. Comprehensive consent management capabilities provide a way for banks to compete by turning the new open banking ecosystem to their advantage.
Which Banks Offer Behavioral Authentication?
Banks are able to provide increasingly amazing user experiences based on the technical capabilities of their authentication technology as well as their general attitude and culture towards security and CX. Some of the most advanced banks, those we have identified as “Stage 3,” are already harnessing the power of data-driven behavioral authentication. Others have begun to put the fundamental CIAM technology in place to support an evolution toward a more data-driven approach. The table below summarizes the characteristics we have identified among banks spread across the authentication capability spectrum.
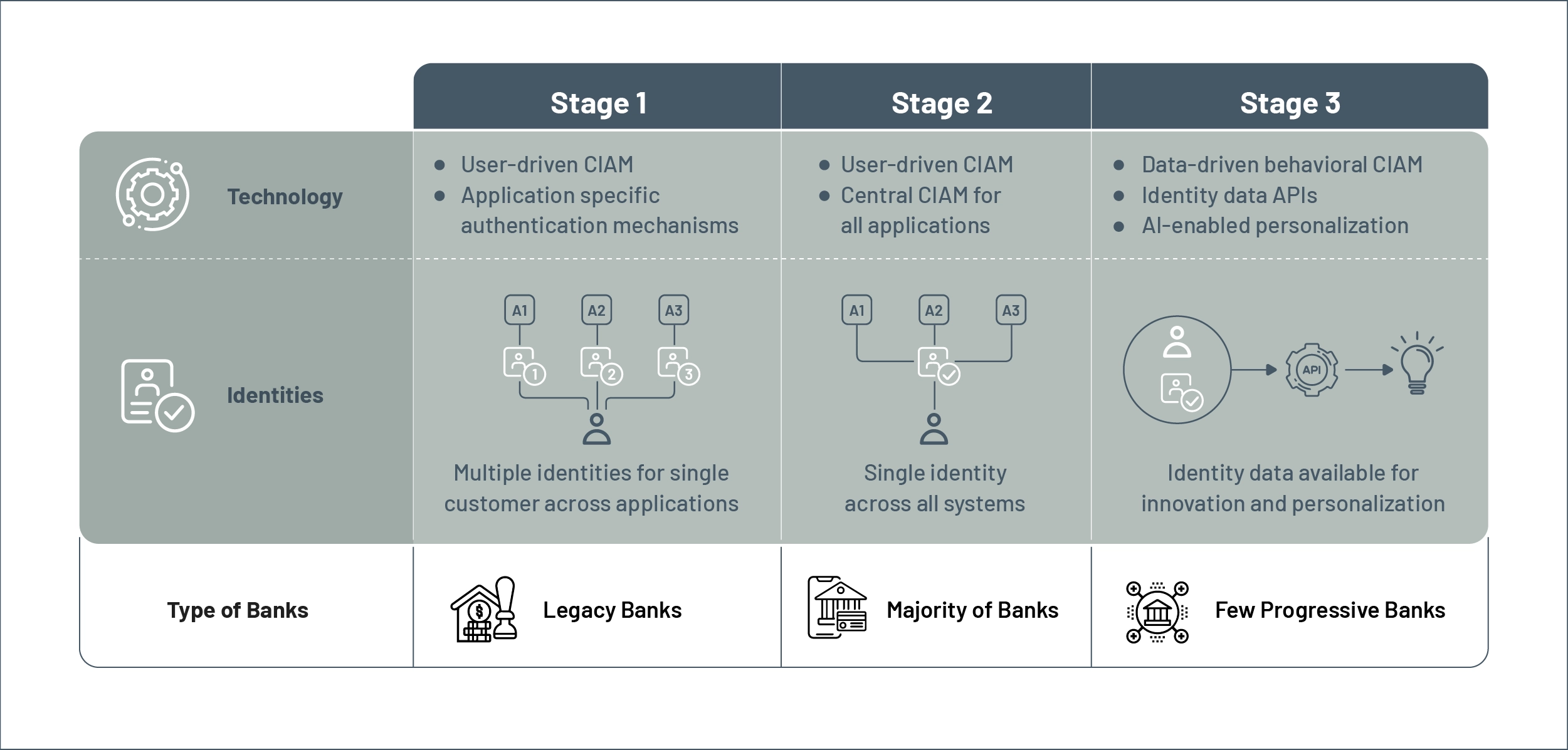
Figure 10: Authentication capability spectrum of banks worldwide
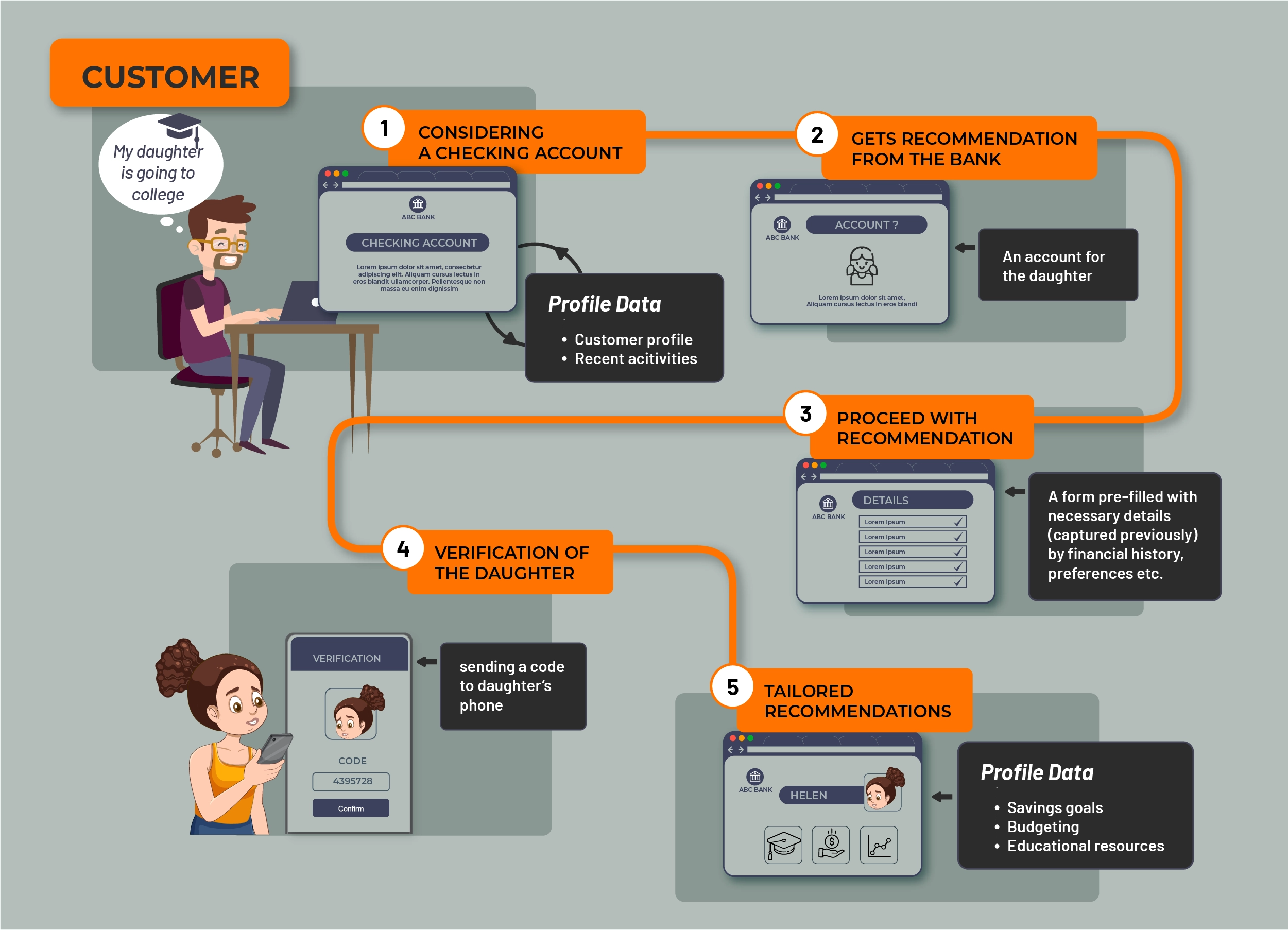
Figure 11: A typical stage 3 bank customer journey
Improving Security and Customer Experience in a Virtuous Cycle
A good example of a stage 3 bank is Starling Bank, one of the UK's most popular challenger banks. In a recent interview, Starling’s Chief Technology Advocate Jason Maude said, “At Starling, we’ve got rid of this need for balance between security and CX. We now have a system that says both aspects (security, reliability, customer safety, and regulatory compliance, along with delivering new products and features and delighting customers) are very important, so let's go for both. We built a system where these two things are mutually reinforcing instead of contradicting each other. So banks should stop envisioning this as a balance and start envisioning it as a virtuous circle.”
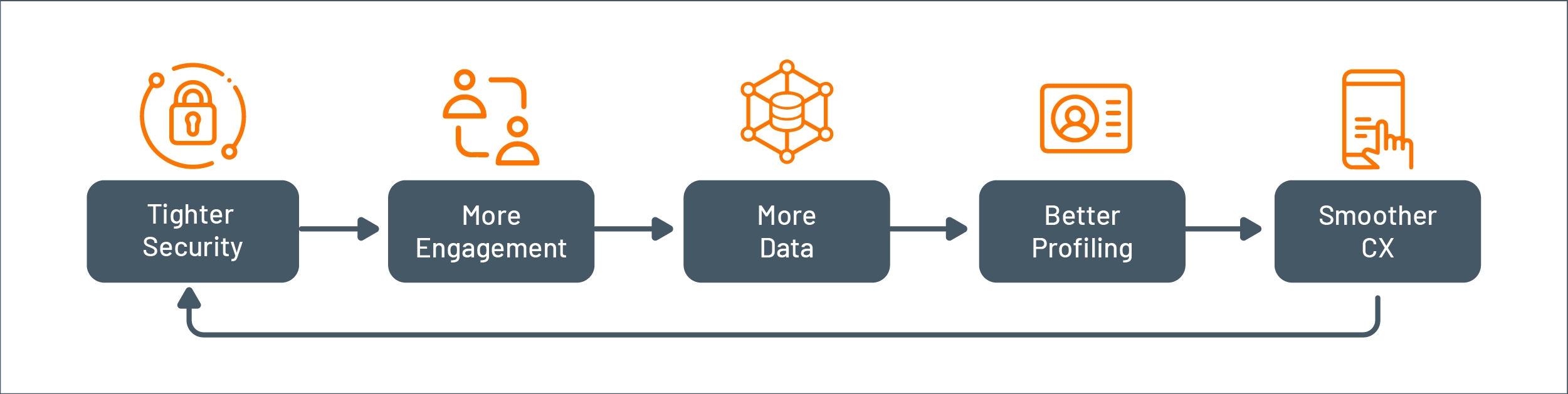
Figure 12: Virtuous cycle of security and CX improvement
Conclusion
Until now, the high-level of security and privacy required to protect customers has hindered banks’ ability to deliver a great CX to them on a large scale. The user-driven CIAM systems that most banks rely on require customers to provide information each time verification is needed for a transaction. However, the emergence of CIAM solutions that support data-driven behavioral authentication now offers the potential for banks to provide seamless, personalized experiences that meet and eventually even exceed those of leading online retail and entertainment companies. By fully utilizing data, banks will have a stronger foundation than ever to build customer loyalty, trust, and value.

