Discover SAML endpoints and configs in Asgardeo
# Discover SAML endpoints and configs in Asgardeo
You can follow this document to obtain required information and the configurations to:
- Integrate sign in with Asgardeo for your SAML web application
- Build login with Asgardeo using a SAML supported library
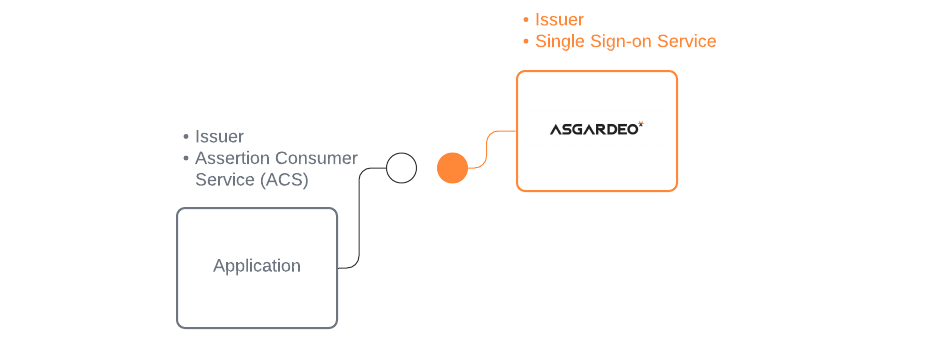
When configuring SAML based sign in with Asgardeo, you need to know:
- SAML IdP endpoints of Asgardeo
- Issuer of Asgardeo
- The public certificate of Asgardeo
# Prerequisite
To get started, you need to have an application registered in Asgardeo. If you don't have an app registered, go to Asgardeo Console (opens new window) to register a SAML application.
# Get SAML configs
You need to know the SAML IdP configurations of Asgardeo if you want to add SAML login to your application.
There are two options for a SAML application to get the SAML IdP configurations of Asgardeo:
# Use SAML metadata
SAML metadata (opens new window) is an XML document which contains information necessary to integrate a SAML application with a with SAML supported identity provider.
The SAML IdP metadata document contains:
Endpoints (single sign-on URLs, single logout URLs, etc)
Supported bindings
IdP identifiers (entityID or sometimes called Issuer)
Public certificate
Sample SAML IdP metadata of Asgardeo
<?xml version="1.0" encoding="UTF-8"?>
<EntityDescriptor
xmlns="urn:oasis:names:tc:SAML:2.0:metadata" entityID="accounts.asgardeo.io/t/{organization_name}">
<IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol" validUntil="2021-07-07T07:01:06.536Z">
<KeyDescriptor use="signing">
<KeyInfo
xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIC/jCCAeagAwIBAgIECXIstjANBgkqhkiG9w0BAQQFADBBMRAwDgYDVQQDDAdiaWZyb3N0MQ0w
CwYDVQQLDAROb25lMQ8wDQYDVQQKDAZOb25lIEwxDTALBgNVBAYTBE5vbmUwHhcNMjEwMzIwMDYz
NTU5WhcNMzEwNDE3MDYzNTU5WjBBMRAwDgYDVQQDDAdiaWZyb3N0MQ0wCwYDVQQLDAROb25lMQ8w
DQYDVQQKDAZOb25lIEwxDTALBgNVBAYTBE5vbmUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
AoIBAQCL+LfgKAXwhl3x7buxjeUmRfozJbt7aggfR/86WfB+1N1L5ICaYgybTpB3KEOvR/JxO41H
2GOwSFKb15xLmRmH2qy598tvU3TjUyXftUTqp44o/gChy9iavSu2kfRNSCped0N4UAAXegtWFROi
TD0iT5PbdwQ8MDyAwKZB/s2N7t82xDpoK7PO99R6Re9GcOX/tkAeBvD/SDK6MgnXU2UqI1uYJ0ow
BOfrxPBDhTlEkP34hPTOLNabVyJX5k5zXYvwCxQj5AWMudSUzhLjZfWiPRNqjWgv1XxAYBIccgYq
on1jG++e7Fod3jY0UUclzAHiguWKuM7Ijkd8plEUTgXNAgMBAAEwDQYJKoZIhvcNAQEEBQADggEB
AEIeJ9o5QYlRV2KJN5bLL7s6GV3hkYMIrzDoxHFgSvEt2XJULHWj3yvKe1hk/HzEII79fYYKS6xJ
v7MORegQP/zFCD8oAHt/3lnhrG1yM/SQDe60Kd5emWqLqMxNQBmmaYQDTY7F5PIdC9KJ/EeKIoz2
P2QlT5TNOcj9chtRHtsohNNv6Nkew6HZ49Xlm4BsFxhP6J5YPExV4bBw+RsHeiNdcxXNGaNtD5n2
L4KOHbmKddsL1x/KZ4Q67xzaS50IhNnfC84pOFxmYT2FsB02ZuVv97UsNF+8xv+GIN3qc+pIJEWd
HFY29KP4da//BDdQrftzYCATe37Um09id/0KMGs=</X509Certificate>
</X509Data>
</KeyInfo>
</KeyDescriptor>
<ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://api.asgardeo.io/t/{organization_name}/samlartresolve" index="1"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://api.asgardeo.io/t/{organization_name}/samlsso" ResponseLocation="https://api.asgardeo.io/t/{organization_name}/samlsso"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://api.asgardeo.io/t/{organization_name}/samlsso" ResponseLocation="https://api.asgardeo.io/t/{organization_name}/samlsso"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://api.asgardeo.io/t/{organization_name}/samlsso" ResponseLocation="https://api.asgardeo.io/t/{organization_name}/samlsso"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://api.asgardeo.io/t/{organization_name}/samlsso"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://api.asgardeo.io/t/{organization_name}/samlsso"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://api.asgardeo.io/t/{organization_name}/samlsso"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://api.asgardeo.io/t/{organization_name}/samlsso"/>
</IDPSSODescriptor>
</EntityDescriptor>
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
There are two ways to get the SAML IdP metadata of Asgardeo.
Based on the capability of your SAML application or library, you can choose either approach.
# Use File Based Metadata
To download the SAML metadata file of your organization in Asgardeo,
In the Asgardeo Console, Select Applications.
Select the SAML application from the application view.
Go to the Info section.
Click Download IdP Metadata to download the metadata xml file.

# Use URL Based Metadata
You can use below endpoint URL to get the SAML IdP metadata information.
https://api.asgardeo.io/t/<organization_name>/identity/metadata/saml2
Sample endpoint URL
https://api.asgardeo.io/t/bifrost/identity/metadata/saml2
When integrating Asgardeo as a SAML IdP in Salesforce, be sure to add the SAML metadata URL to the Salesforce remote site settings (opens new window) to recognize it as an authorized network address.
# Get SAML configurations of Asgardeo from Console
Some applications and SDKs do not have the capability to dynamically resolve endpoints from SAML metadata file. You need to configure endpoints manually to support them.
You can login to Asgardeo Console (opens new window) and get endpoints of Asgardeo.
In the Asgardeo Console, click Applications.
Select the SAML application from the application view.
Go to the Info section of the application and finds the below server information related to your organization:
- Issuer : Issuer name of Asgardeo
- Single Sign-On : Sign-on URL of Asgardeo
- Single Logout : Logout URL of Asgardeo
- IdP certificate : Public certificate of Asgardeo
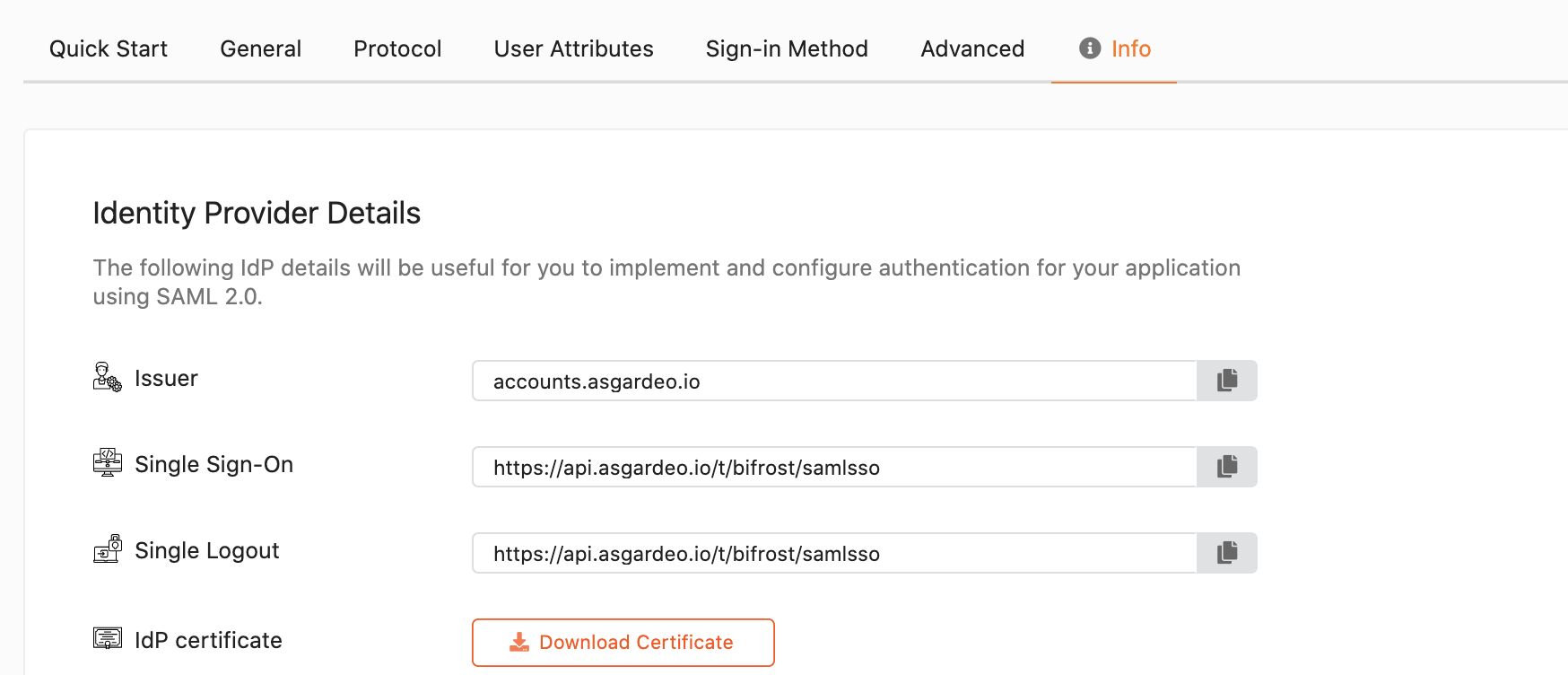
You can download the certificate of Asgardeo from IdP certificate.
# What's next?
Now you've integrated your SAML web application. You also can:
