Connect a remote user store
# Connect a remote user store
If you have connected a remote user store before 7th February 2023, you will have Read-Only access for the user store. If you need Read-Write access for your user store on Asgardeo,
- Delete the existing remote user store.
- Register a remote user store again with Read/Write access type.
- Set up the remote user store with the latest user store agent.
You can connect your on-premise user store to Asgardeo and onboard users and groups from it. Note that this user store connection is read-only, which means you cannot use the Asgardeo Console to modify this user store.
Administrators get the opportunity to manage access to business applications and manage users and groups based on the access type of the user store.
Follow the guide below to set up a remote user store in Asgardeo.
# Prerequisites
An organization in Asgardeo. Create an organization if you don’t have one already.
An on-premise user store. Currently, Asgardeo supports:
- Lightweight Directory Access Protocol (LDAP)
- Active Directory (AD)
To run the user store agent, you need to have:
- JAVA 8 or JAVA 11 installed locally
- JAVA_HOME configured correctly
Requirements
Recommended hardware requirements
CPU cores 2Storage 500 MBof free space on disk.Operating System The connector can run on Windows or Linux. RAM 1 GBConnectivity methods
Protocol Web socket Port 443
# Register a remote user store
To configure a remote user store for your organization:
On the Asgardeo Console, go to User Attributes & Stores > User Stores.
Click Connect userstore to open the following:
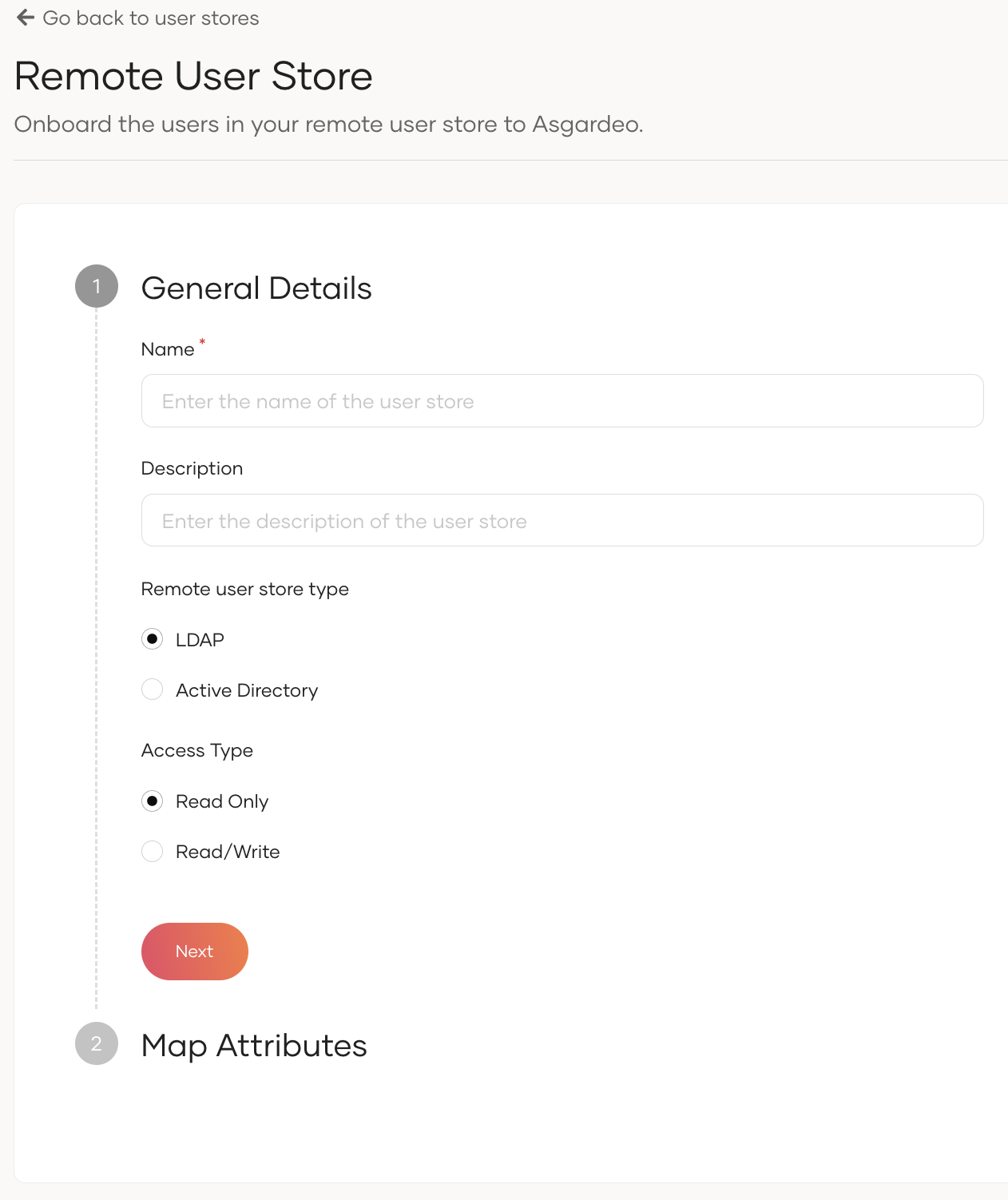
Enter the following details about the user store.
Name A unique name to identify your user store. Description A description for the user store. Remote user store type Select your user store type Access Type Select the access type of the user store. It can be any one of the following:
- Read-only
- Read/Write
Note : The access type of the user store cannot be modified after creation.Click Next and under Map Attributes, map Username and User ID attributes to that of your user store.
These two attributes need to be mapped correctly for proper authentication.
Username- This attribute is used as the user identifier. Provide an attribute that identifies your user in your on-premise user store. For the best experience, use a username that satisfies validation rules in Username Validation section.User ID- This attribute is used to uniquely identify a user entry. Provide an attribute that uniquely identifies a user entry in your user store.
Click Finish to complete the registration.
# Set up the remote user store
After registering the user store, you’ll be redirected to the Setup Guide of the user store agent.
To assemble and configure the user store agent bundle:
Download the user store agent.
Configure the properties and connection details of the local user store by following these steps:
Unzip the downloaded user store agent.
Go to the root directory of the user store agent and open the
deployment.tomlfile.Update the configurations of the
deployment.tomlfile according to your user store settings. A sample configuration is given below for reference.[user_store] type = "ldap" base_dn = "dc=wso2,dc=org" connection_url = "ldap://localhost:10391" connection_name = "cn=admin,dc=example,dc=org" connection_password = "adminpassword" user_id_search_filter = "(&(objectClass=inetOrgperson)(uid=?))" user_name_list_filter = "(objectClass=inetOrgperson)" user_id_attribute = "uid" user_name_attribute = "cn" user_name_search_filter = "(&(objectClass=inetOrgperson)(cn=?))" password_hash_method = "PLAIN_TEXT" group_search_base = "ou=Groups,dc=example,dc=org" group_name_attribute = "cn" group_name_search_filter = "(&(objectClass=groupOfNames)(cn=?))" group_name_list_filter = "(objectClass=groupOfNames)" group_id_attribute = "gid" membership_attribute = "member"1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18Refer remote user store properties for the complete list of user store configurations.
Return to the Asgardeo Console and, click Generate Token to create an installation token. The installation token is essential to run the user store agent.
Copy the installation token and save it in a safe location. You won't be able to see it again!
This token has no expiry time, but in case you lose or forget it, you can regenerate an installation token.
To start the user store agent, navigate to its root directory and run one of the following commands based on your operating system:
Linux/OSx:
sh wso2agent.sh1Windows:
wso2agent.bat -- run1
Enter the installation token generated in the previous step when prompted.
(Optional) Run the user store agent as a background process
- Create a file named
accessTokenin the root directory of the agent. - Add the installation token obtained from the previous step.
- Run the user store agent.
Linux/OSx:
sh wso2agent.sh start1Windows:
wso2agent.bat start1
